What is the ARC-Authentication-Results header used for?

Matthew Whittaker
Co-founder & CTO, Suped
Published 24 Feb 2025
Updated 12 Oct 2025
7 min read

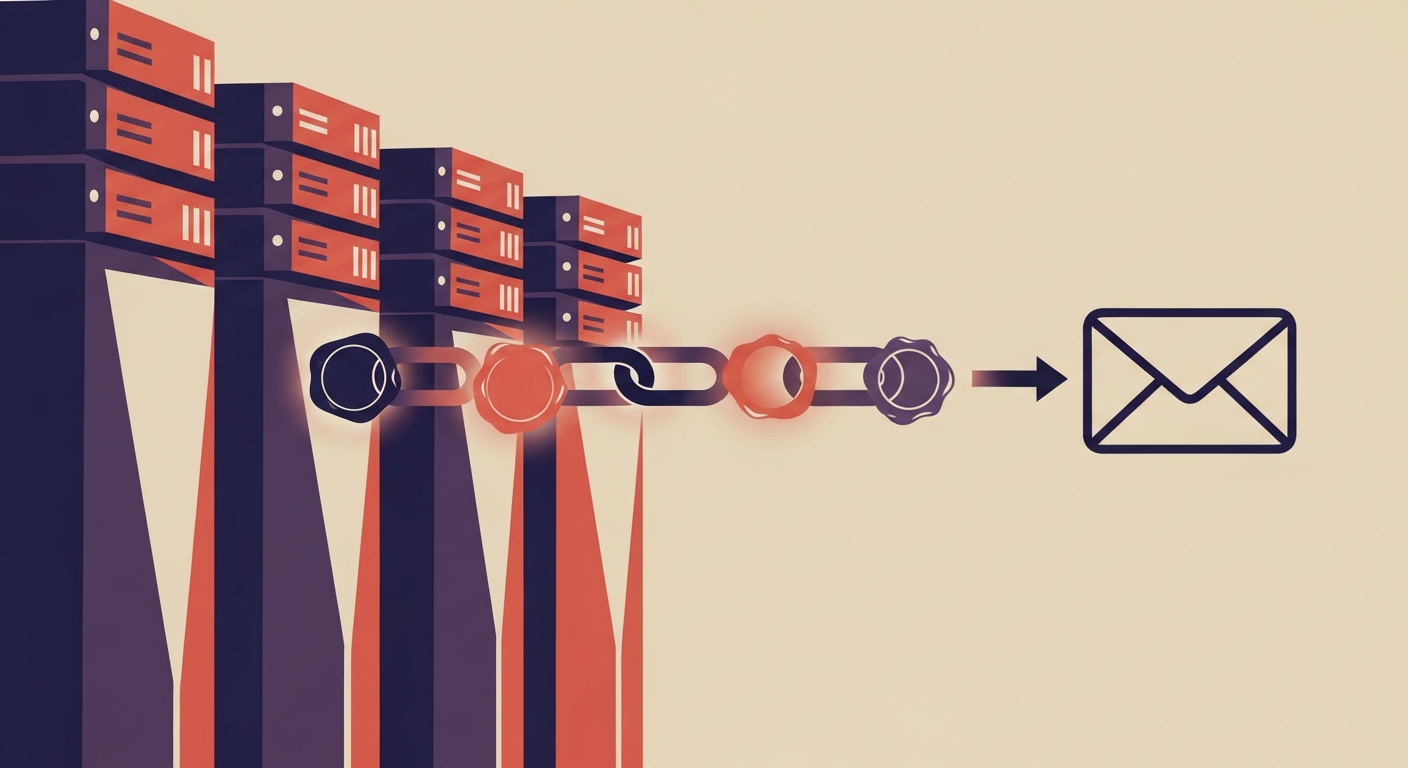
ARC-Authentication-Results: i=1; mx.google.com; dkim=pass header.i=@example.com header.s=s1 header.b=AbCdEfGh; spf=pass (google.com: domain of user@example.com designates 203.0.113.42 as permitted sender) smtp.mailfrom=user@example.com; dmarc=pass (p=quarantine sp=quarantine dis=none) header.from=example.com
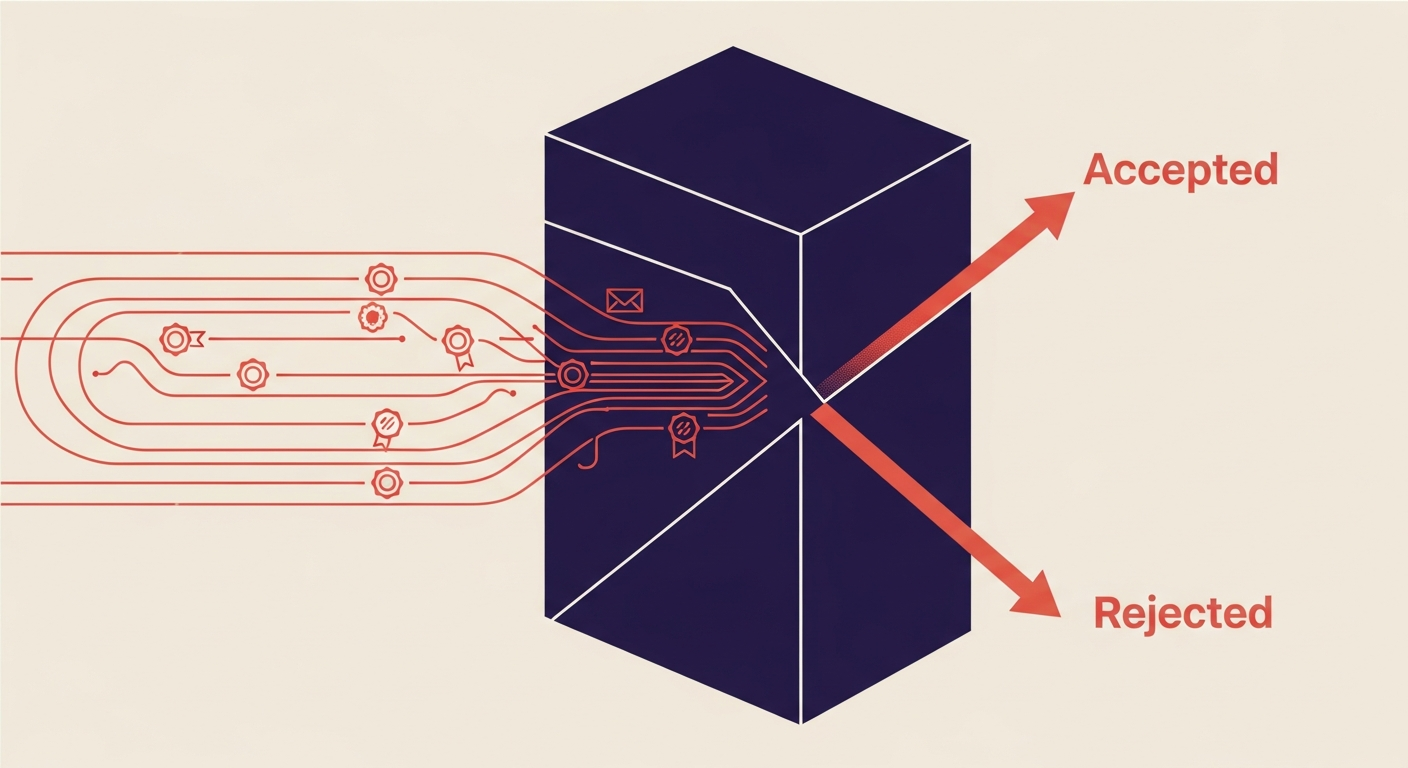
 Microsoft Defender and other major mail providers utilize ARC to enhance their spam filtering and ensure legitimate forwarded emails are delivered. Without ARC, legitimate messages, particularly those sent through mailing lists that modify the message, would often fail DMARC and be blocked or sent to spam.
Microsoft Defender and other major mail providers utilize ARC to enhance their spam filtering and ensure legitimate forwarded emails are delivered. Without ARC, legitimate messages, particularly those sent through mailing lists that modify the message, would often fail DMARC and be blocked or sent to spam. generous free plan provides access to essential DMARC monitoring tools, allowing you to quickly identify and fix issues. Our SPF flattening feature also ensures you stay within SPF lookup limits, further boosting your email deliverability. Don't let forwarded emails end up in spam. Use Suped to maintain trust and ensure your messages always reach the inbox.
generous free plan provides access to essential DMARC monitoring tools, allowing you to quickly identify and fix issues. Our SPF flattening feature also ensures you stay within SPF lookup limits, further boosting your email deliverability. Don't let forwarded emails end up in spam. Use Suped to maintain trust and ensure your messages always reach the inbox.