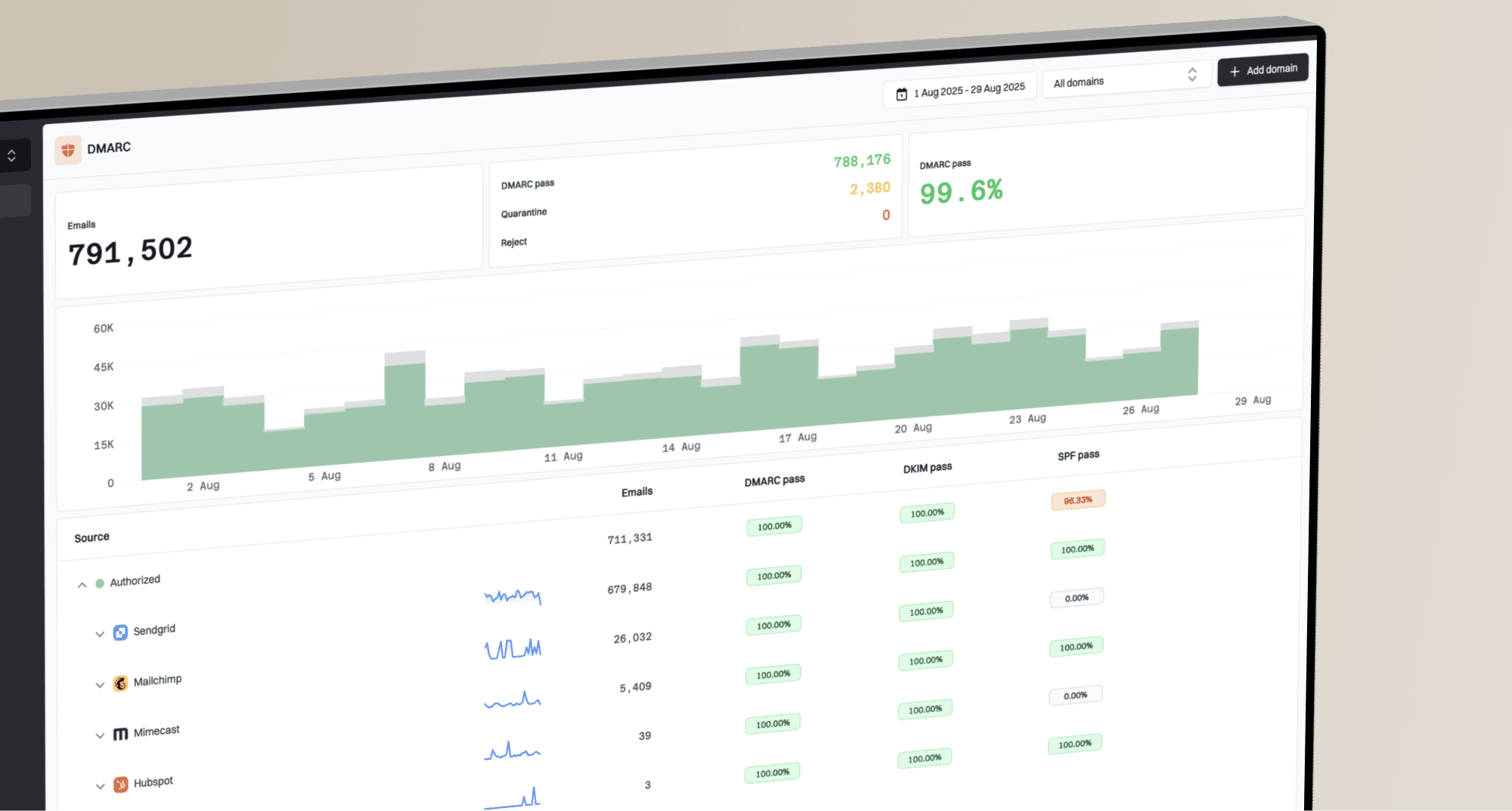
What is the 'arc-authenticated-results' header?

Michael Ko
Co-founder & CEO, Suped
Published 4 Sep 2025
Updated 25 Oct 2025
7 min read

ARC-Authentication-Results: i=1; mx.example.com; spf=pass (sender IP is 192.0.2.1) smtp.mailfrom=sender@example.com; dkim=pass (signature was verified) header.d=example.com; dmarc=pass action=none header.from=example.com;
 Microsoft Defender system might look for specific values like arc=pass and oda=1 in the last ARC-Authentication-Results header to confirm the previous ARC verification and origin domain authentication, as outlined in their documentation.
Microsoft Defender system might look for specific values like arc=pass and oda=1 in the last ARC-Authentication-Results header to confirm the previous ARC verification and origin domain authentication, as outlined in their documentation.
|
|
|
|---|---|---|
pass | The ARC-Seal and its associated authentication results were successfully validated. | Indicates trustworthiness, helps DMARC pass even with SPF/DKIM breaks. |
fail | The ARC-Seal could not be verified, or the chain was broken or manipulated. | Suggests potential tampering, may lead to DMARC failure or spam classification. |
none | No ARC-Seal was present or no ARC evaluation was performed. | ARC cannot provide any additional trust signals for DMARC evaluation. |