There are few things more frustrating than carefully crafting an email, hitting send, and then receiving a bounce-back message with a cryptic error: 'DMARC verification failed'. It’s a message that stops your communication in its tracks and can leave you wondering what went wrong. You sent a legitimate email from a legitimate address, so why was it rejected? This is a common hurdle for businesses and individuals alike, especially as email providers like Google and Yahoo tighten their security requirements.
This error means your email failed an important security check called DMARC, which stands for Domain-based Message Authentication, Reporting, and Conformance. It's a technical standard designed to protect your domain from being used for phishing and spoofing attacks. While its goal is to increase trust and security, a small misconfiguration can cause your own valid emails to be blocked. Understanding why it fails is the first step to ensuring your messages land where they're supposed to.

At its core, a DMARC fail error indicates that a receiving email server checked your domain's DMARC policy and found that the incoming email did not meet the authentication requirements. DMARC doesn't work alone; it relies on two other email authentication standards: SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail). For an email to pass DMARC, it must pass either SPF or DKIM, and, critically, it must also be 'aligned'.
This concept of 'alignment' is where most people get tripped up. It’s not enough for an SPF or DKIM check to simply pass. The domain used for the authentication check must match the domain seen in the 'From' header of the email, the one your recipient sees. For SPF, this means the domain in the hidden 'Return-Path' address must align with the 'From' domain. For DKIM, the domain specified in the DKIM signature's 'd=' tag must align with the 'From' domain.
Think of it like this: SPF is like telling the bouncer who is on your guest list (which IP addresses can send for you). DKIM is like giving your guests a special, unforgeable stamp. DMARC is the head of security who checks if a person's ID (the 'From' address) matches someone on the guest list or has the correct stamp. If a person with a valid stamp for a different event shows up, they still won't get in. That mismatch is an alignment failure, and it's a very common cause of DMARC failures.
The receiving server looks at your DMARC policy, which is published in your DNS, to decide what to do with a failing email. If your policy is set to 'p=reject', the email will be bounced. If it's 'p=quarantine', it will likely be sent to the spam folder. If it's 'p=none', the email will be delivered, but you’ll still get a report on the failure. This is why understanding the way DMARC failures are handled is crucial for troubleshooting.
When you see that your emails are bouncing back due to DMARC, it almost always comes down to a configuration issue. These are not malicious attacks but simple oversights in your setup. Here are some of the most frequent culprits:
Alignment issues with services like Amazon SES or Google Workspace are particularly common. These platforms might handle the basic SPF and DKIM setup for their own domains, but you must take extra steps to align them with your 'From' domain. This usually involves adding specific CNAME or TXT records provided by the service to your own domain's DNS settings.
If you don't resolve these issues, your domain could end up on a blacklist (also known as a blocklist), severely impacting your deliverability. A DMARC reject policy is a strong signal, and mail servers take it seriously. Consistent failures suggest poor email hygiene, which can damage your sender reputation beyond just the emails that are immediately blocked.
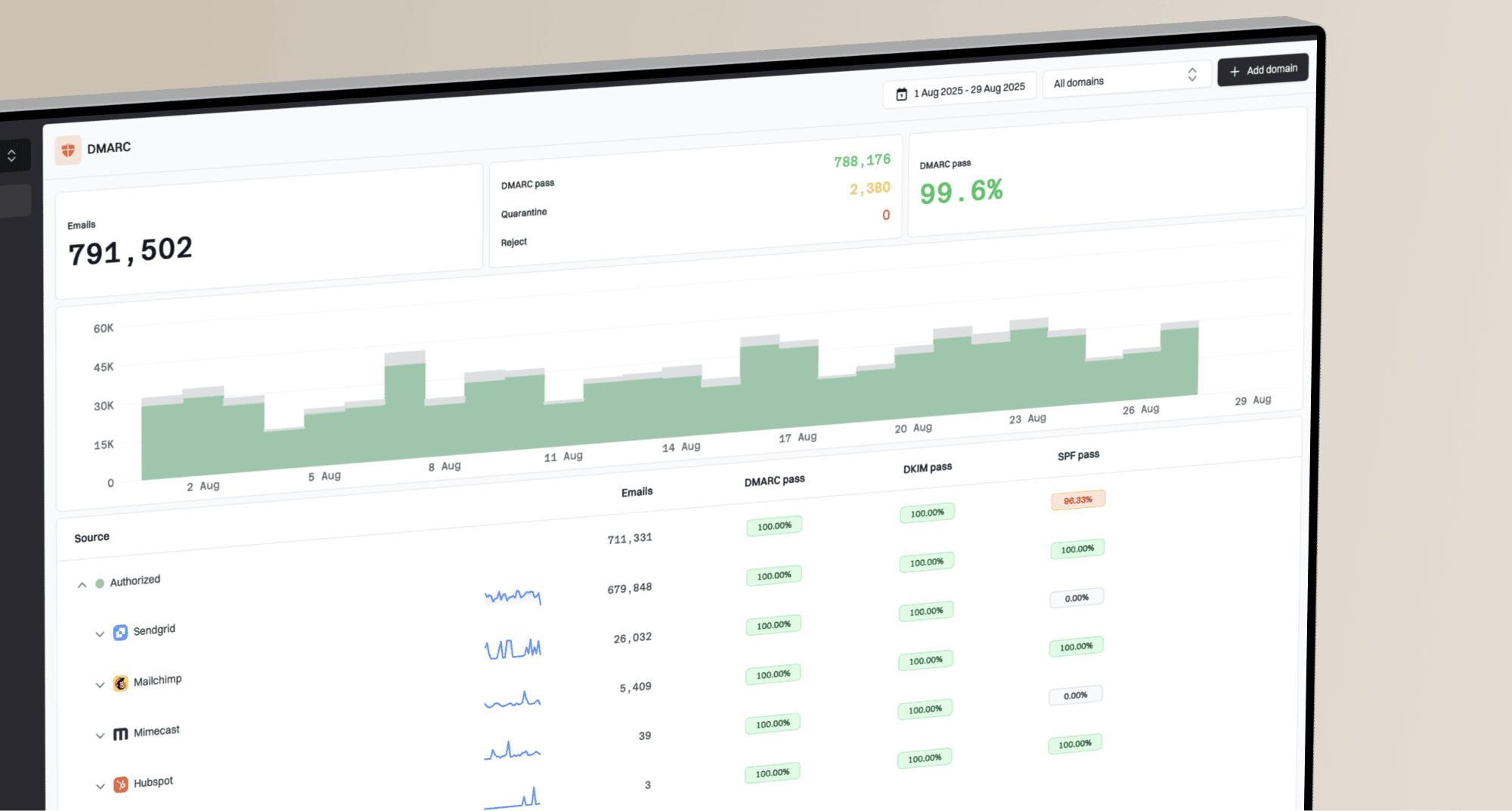
Fixing DMARC failures is a methodical process, not a quick flip of a switch. The first and most crucial step is to gather data. This is where DMARC reports come in. Your DMARC record should include a 'rua' tag with your email address (e.g., rua=mailto:dmarc-reports@example.com). This tells receiving servers where to send aggregate reports about your email traffic.
These reports, while incredibly detailed, are sent as XML files that are difficult for humans to read. This is where a DMARC monitoring service becomes invaluable, as it parses these reports into user-friendly dashboards. By analyzing the reports, you can see which IP addresses are sending mail on your behalf and whether they are passing or failing SPF and DKIM alignment. This allows you to identify all your legitimate sending services, including the ones you might have forgotten about.
The golden rule is to start with a monitoring policy: p=none. This ensures your emails are still delivered while you collect data. Once you have identified a legitimate sender that is failing, you must check the SPF and DKIM settings for it. Go to that service's documentation and find the specific DNS records you need to add to your domain. After adding the records and seeing in your reports that your legitimate mail is passing and aligned, you can confidently move to a policy of p=quarantine and, eventually, p=reject.
Seeing a 'DMARC verification failed' message can be alarming, but it’s a solvable issue. It points not to a flaw in the system, but a gap in your domain's configuration. The solution lies in understanding that DMARC is a gatekeeper that relies on the twin pillars of SPF and DKIM, and more importantly, their alignment with your 'From' domain. Any discrepancy here is the root cause of the problem.
The path to resolution is paved with data. By starting with a p=none policy and diligently analyzing your DMARC reports, you can systematically identify and authorize every legitimate service that sends email for your domain. It’s a process of discovery, configuration, and verification. Rushing to a p=reject policy without this groundwork is a recipe for blocking your own important communications.
Ultimately, getting DMARC right is a significant achievement. It secures your domain against impersonation, builds trust with mailbox providers, and boosts your email deliverability. That error message, once a source of frustration, can become a catalyst for creating a more secure and reliable email ecosystem for your brand.