When you send a letter, you probably don't worry about someone else grabbing it, changing the words, and sending it along. You also probably don't worry about a scammer sending thousands of letters with your return address on them. On the internet, these things are very real possibilities. Email wasn't originally built with strict identity verification, making it easy for malicious actors to impersonate people and brands.
This is where the email security trio, SPF, DKIM, and DMARC, comes into play. If you've ever heard these acronyms and felt a bit lost, you're not alone. They can seem complicated, but their purpose is actually quite simple: to prove that an email is really from who it says it's from. Think of them as the three essential guards for your email, protecting your domain from being used for phishing and spam.
Imagine your domain name (like `suped.com`) as your company headquarters. You don't want just anyone sending official-looking mail from your address. You need a system to verify every message. Without it, anyone could send an email pretending to be `ceo@yourcompany.com`, asking for sensitive information or tricking your customers.
Let's break down each of these components one by one. Understanding them is the first step towards securing your email, protecting your brand's reputation, and improving your email deliverability. The good news is, you don't need to be a security expert to grasp the basics.
Let's start with SPF. Think of SPF as a guest list for a party you're hosting at your house. You give the bouncer at the door a list of names, and only the people on that list are allowed in. Anyone else who shows up claiming to be your friend gets turned away. It’s a straightforward way to control who can enter.
In email terms, the SPF record is that guest list. It's a simple text file you add to your domain's DNS settings. This file lists all the IP addresses (servers) that are authorized to send email on behalf of your domain. When a receiving mail server gets an email from you, it checks your SPF record. If the server that sent the email is on your list, the email passes the SPF check. If not, it's considered suspicious.
v=spf1 include:_spf.google.com ~allSPF is a great first step, but it has a key weakness: it can break when an email is forwarded. If you email a friend and they automatically forward it to another address, the forwarding server's IP address won't be in your SPF record. This can cause the forwarded, but still legitimate, email to fail the SPF check. This is one reason why SPF alone is not enough.
Next up is DKIM. If SPF is the guest list, think of DKIM as a special, tamper-proof wax seal on an envelope. Before you send a royal decree, you stamp it with your unique seal. Anyone who receives it can see the unbroken seal and know two things: the letter really came from you, and nobody opened it and changed the contents along the way.
DKIM works by adding a digital signature to your email's header. This signature is created using a private key that only you have access to. The corresponding public key is published in your domain's DNS records. When a receiving mail server gets your email, it finds the public key to verify the signature. If the signature is valid, the server knows the email is authentic and hasn't been altered. This process is a core part of modern email authentication methods.
The biggest advantage of DKIM is that the signature is part of the email itself, so it travels with the message. This means that even if the email is forwarded, the DKIM signature remains valid, overcoming the main weakness of SPF. However, a malicious actor could still set up DKIM for their own domain and send spam; it just proves the email is from *their* domain, not necessarily a reputable one. That's why we need one more piece to the puzzle.
Finally, we have DMARC. If SPF is the guest list and DKIM is the tamper-proof seal, then DMARC is the head of security who takes instructions directly from you. DMARC doesn't authenticate anything itself. Instead, it looks at the results from SPF and DKIM and then tells the receiving server what to do based on your policies.
DMARC checks for something called "alignment." It ensures that the domain used in the "From" address that the user sees actually matches the domain that passed the SPF or DKIM check. This prevents a common trick where an email passes SPF/DKIM for one domain, but shows a different, spoofed domain in the From field. It ties everything together to stop phishing and spoofed email problems.
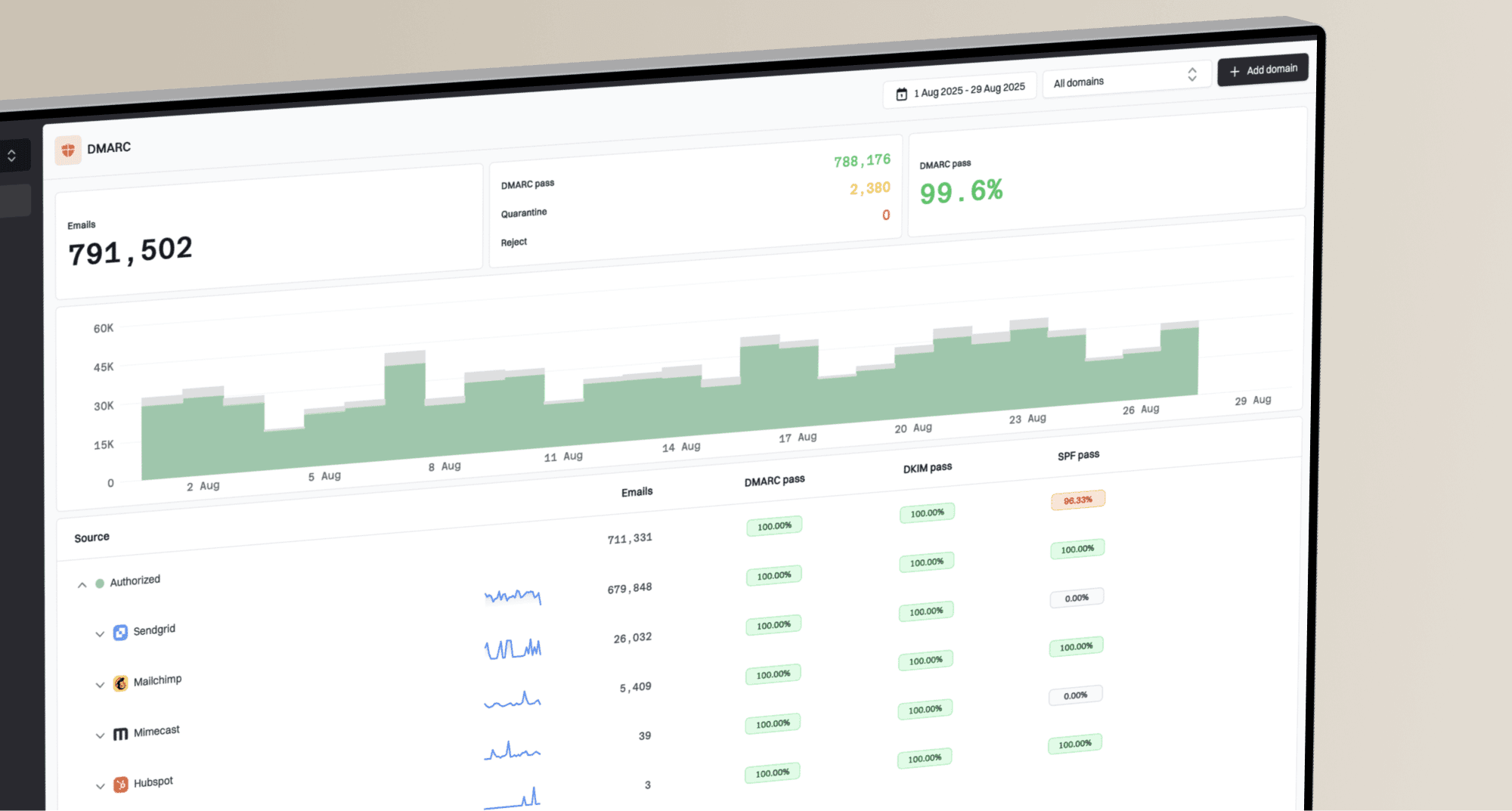
The best part of DMARC is its reporting feature. It instructs mail servers around the world to send you detailed reports about all email—both legitimate and fraudulent—being sent using your domain. These reports are invaluable for identifying all your legitimate sending services and spotting abuse. Monitoring these reports is the only way to safely move from `p=none` to `p=reject` without accidentally blocking your own emails.
So, to put it all together: SPF provides a list of approved senders, DKIM provides a tamper-proof seal, and DMARC provides the instructions for what to do with messages that fail these checks. They are not competing technologies; they are designed to be used together as a complete system.
Implementing all three has become essential, not just for security but also for deliverability. Major mailbox providers like Google and Yahoo now require authentication to deliver mail, especially for bulk senders. Without proper setup, your marketing campaigns, transactional emails, and even day-to-day communications could end up in spam or get blocked entirely. It's the foundation of a strong sender reputation.
By setting up SPF, DKIM, and DMARC, you take control of your domain's email identity. You're telling the world that you take security seriously, making it much harder for criminals to impersonate you and protecting your customers and your brand's hard-earned trust.