What are the three main ARC header fields?

Michael Ko
Co-founder & CEO, Suped
Published 28 Jun 2025
Updated 16 Oct 2025
7 min read

ARC-Authentication-Results: i=1; mx.example.com; spf=pass (sender IP is 192.0.2.1) smtp.mailfrom=sender.com; dkim=pass (signature was verified) header.d=sender.com; dmarc=pass action=none header.from=sender.com

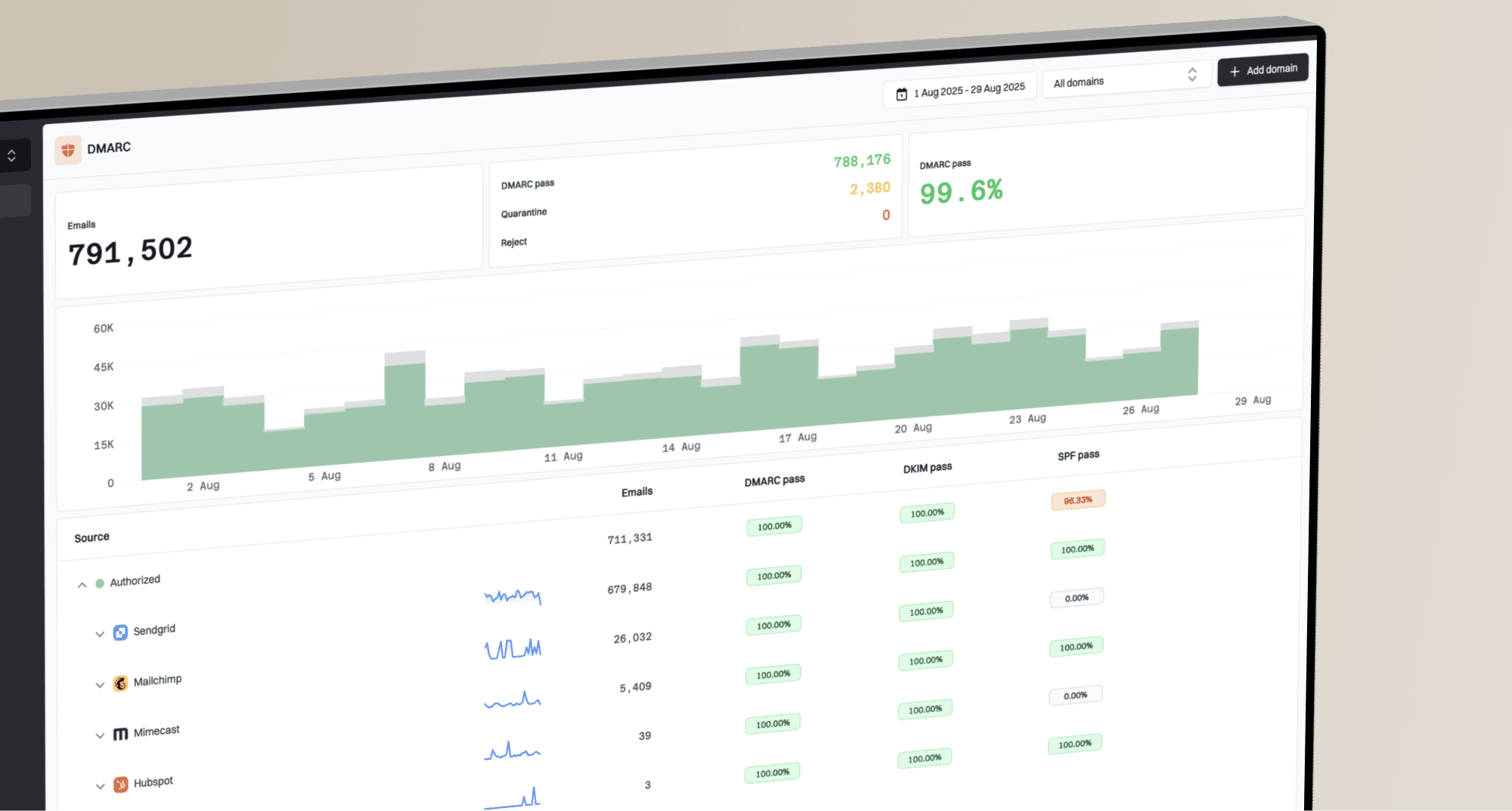
 Suped offer comprehensive DMARC monitoring and reporting, providing insights into ARC validation statuses and helping you fine-tune your email authentication policies. Our AI-powered recommendations help you to quickly identify and resolve issues, ensuring your legitimate emails reach the inbox.
Suped offer comprehensive DMARC monitoring and reporting, providing insights into ARC validation statuses and helping you fine-tune your email authentication policies. Our AI-powered recommendations help you to quickly identify and resolve issues, ensuring your legitimate emails reach the inbox.