What is the role of the 'Authentication-Results' header in ARC?

Michael Ko
Co-founder & CEO, Suped
Published 29 Dec 2024
Updated 20 Oct 2025
5 min read

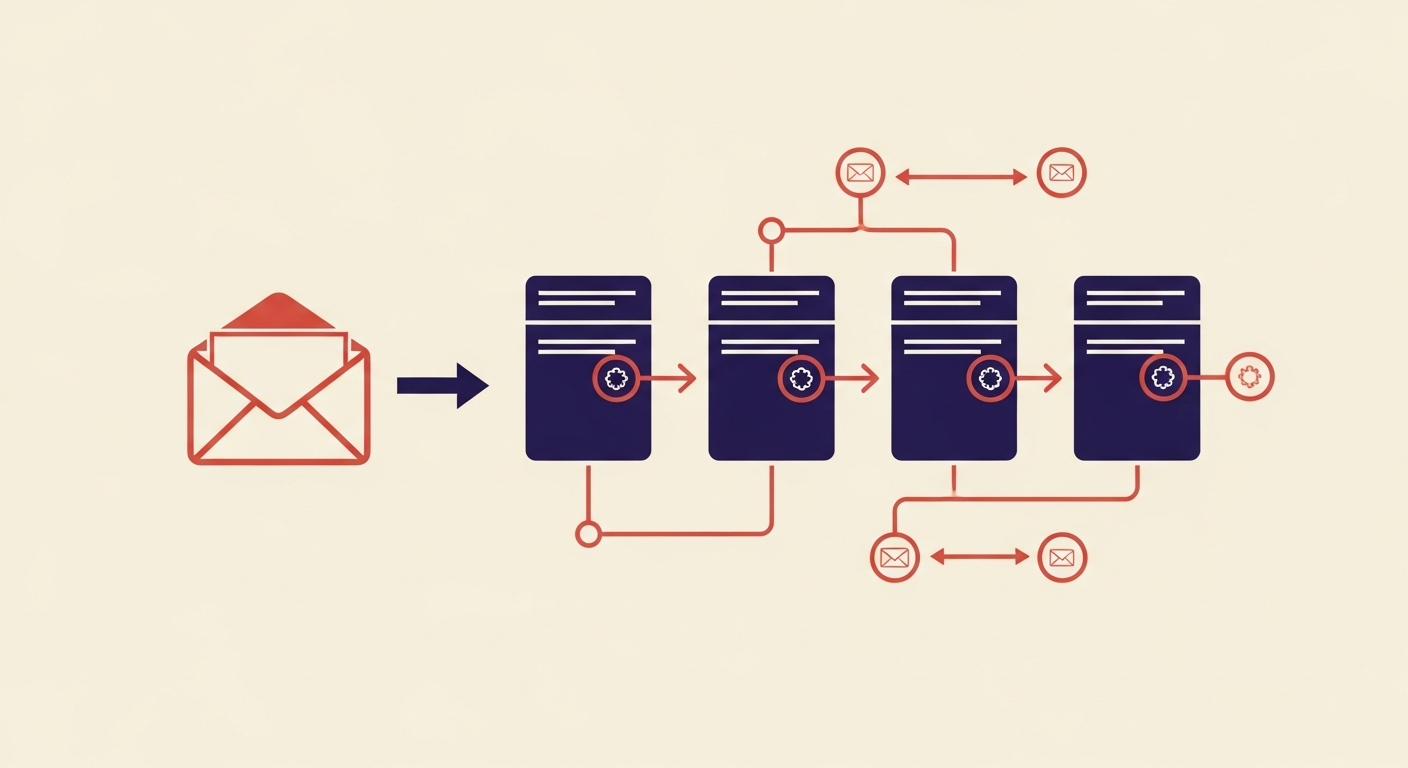
ARC-Authentication-Results: i=1; mx.google.com; spf=pass (google.com: domain of sender@example.com designates 203.0.113.42 as permitted sender) smtp.mailfrom=sender@example.com; dkim=pass header.d=example.com; dmarc=pass (p=none sp=none dis=none) header.from=example.com; arc=none
|
|
|---|---|
none | No ARC signature found, or ARC processing was not performed. |
pass | The ARC chain successfully validated, meaning the email’s integrity was maintained through intermediaries. |
fail | The ARC chain failed validation, indicating tampering or a broken chain of trust. |
temperror | A temporary error occurred during ARC validation, usually due to transient network issues. |