If you're in the email world, you've undoubtedly heard about SPF, DKIM, and DMARC. You've probably already set them up for your domain, following guides and best practices. But setting up the basic records is just the first step. True email authentication mastery goes much deeper, into a landscape of alignment issues, technical limitations, and strategic policy decisions that can make or break your email deliverability and security.
This guide is for those who have moved past the initial setup. We'll explore the nuances that separate a basic configuration from a robust one. We will dive into advanced topics like DMARC alignment, the infamous SPF 10-lookup limit, a safe path to a restrictive policy, and the emerging standards that build upon this foundation. It's time to go beyond the basics and truly secure your email sending reputation.

One of the most misunderstood concepts in DMARC is alignment. It’s not enough for an email to pass SPF or DKIM checks; for DMARC to pass, the domain used for those checks must align with the domain in the visible 'From' address. This is the mechanism that actually prevents spoofing. An email can have a valid SPF record and a valid DKIM signature, but if they are for a different domain than the one your recipients see, DMARC will fail.
For SPF alignment, the domain in the 'Return-Path' (also known as the 'envelope from' or 'MailFrom') address must match the 'From' header domain. This often breaks when using third-party services that handle bounces on their own domain. For DKIM, the domain specified in the signature's d= tag must match the 'From' header domain. This is generally easier to control, as you can often configure your sending services to sign with a key for your domain.
DMARC allows for two alignment modes: relaxed and strict. Relaxed alignment, the default, allows subdomains to align with the parent domain. For example, an email from marketing.example.com can pass DMARC for example.com. Strict alignment requires an exact domain match. Choosing the right mode depends on your organization's email infrastructure and security requirements.
The Sender Policy Framework (SPF) has a well-known and often frustrating limitation: a maximum of 10 DNS lookups are allowed per check. Every time a receiving server evaluates your SPF record, it counts mechanisms like include, a, mx, and redirect against this limit. If your record exceeds 10 lookups, it will result in a permanent error (PermError), and SPF authentication will fail. This becomes a significant problem for businesses that use many cloud services, each requiring its own include.
One advanced technique to manage this is using SPF macros. Macros are variables that can be inserted into an SPF record, which are then replaced with values from the email being processed. For example, you could create a specific subdomain for a vendor and use macros to check the sending IP against a record for that vendor, potentially reducing the number of static include mechanisms in your main record.
v=spf1 include:%{ir}._ip.%{v}._spf.example.com ~allWhile powerful, macros add complexity. An alternative approach is 'SPF flattening', where you resolve all the IP addresses from your include mechanisms into a single record of ip4 and ip6 ranges. However, this creates a maintenance burden, as you must constantly monitor your vendors' sending IPs for changes and update your record accordingly. Failure to do so can cause legitimate emails to be blocked.
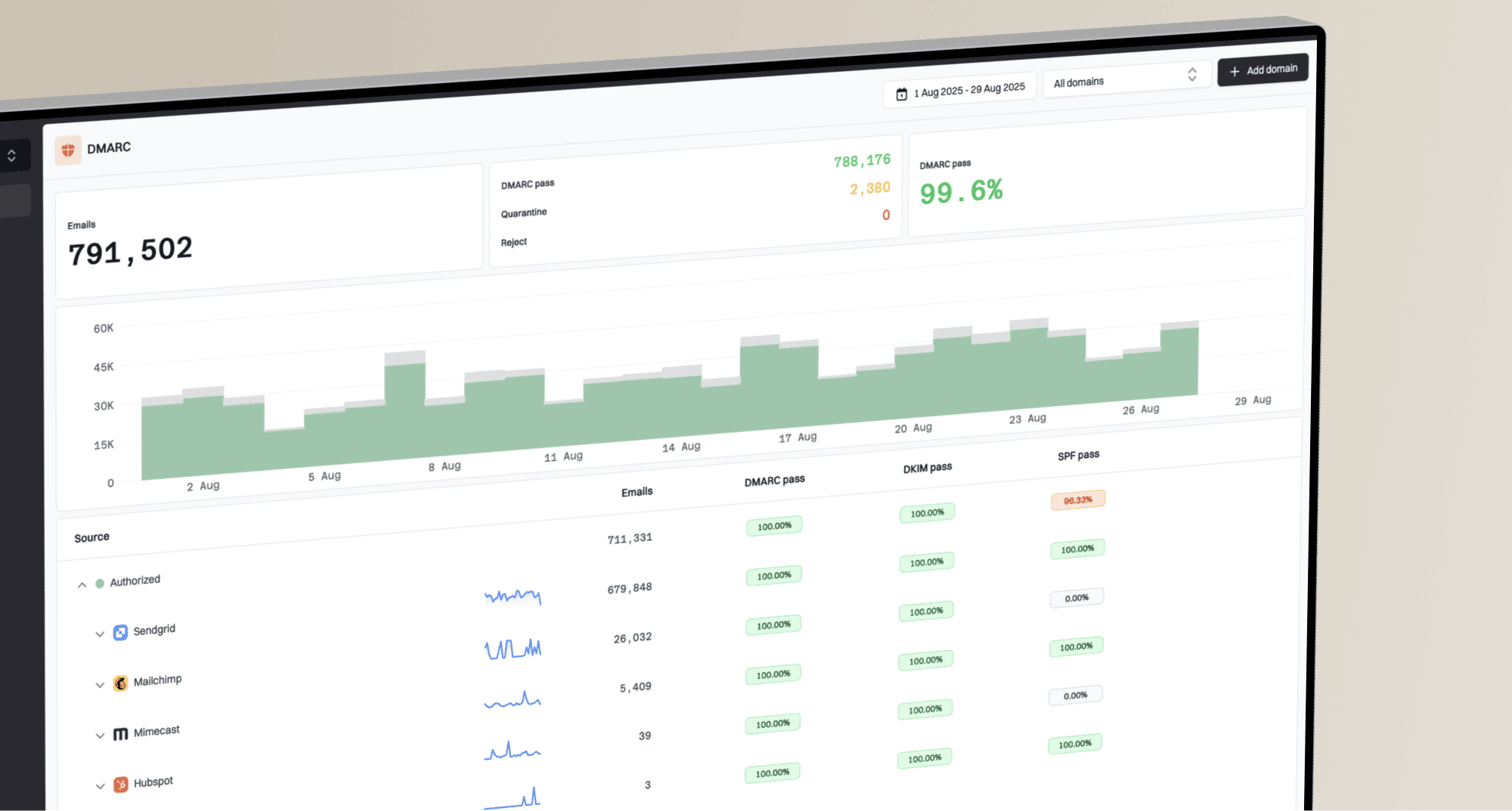
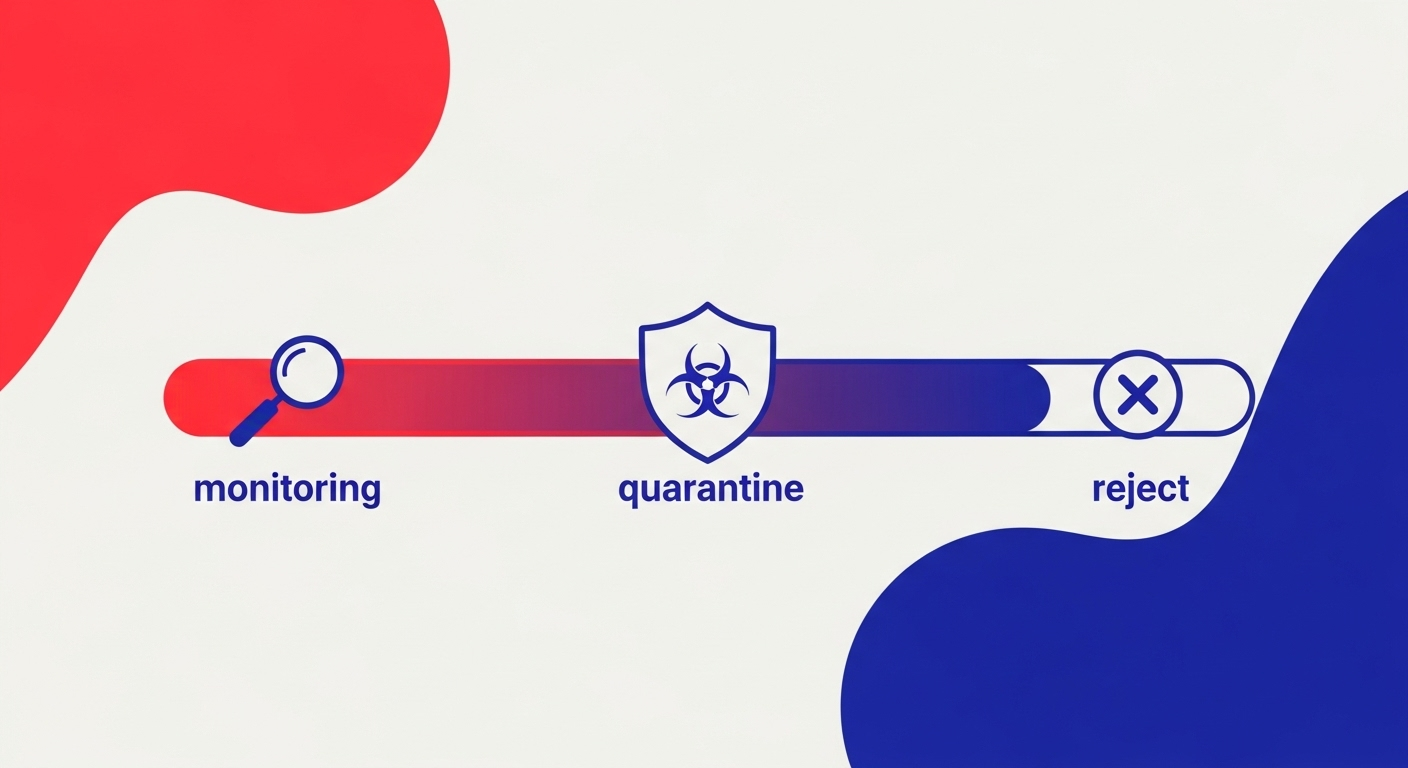
A DMARC record is not a 'set it and forget it' tool. Its true power comes from the reports it generates. By setting your policy to p=none, you enter a monitoring-only mode. This is the crucial first phase. You must use a DMARC monitoring service to parse the aggregate (RUA) reports that mailbox providers send you. These reports give you a complete picture of who is sending email on behalf of your domain, and whether those emails are passing or failing authentication checks.
The goal is to move methodically from p=none to p=quarantine and ultimately to p=reject. Rushing this process is a common mistake that can lead to legitimate emails being sent to spam or blocked entirely. The DMARC policy escalation should only begin after you have identified and correctly configured all your legitimate sending sources to pass DMARC alignment.
Once you have achieved a DMARC enforcement policy, you can explore emerging standards that build upon it. Brand Indicators for Message Identification (BIMI) is a prime example. BIMI is an email specification that allows you to display your company's logo next to your authenticated emails in the recipient's inbox. It acts as a visual verification of your brand's identity and is a powerful way to increase brand recognition and trust.
Implementing BIMI isn't simple. It has strict prerequisites, the most important being a DMARC policy of p=quarantine or p=reject at 100%. You also need a specific SVG Tiny 1.2 format logo hosted publicly, and for many mail providers, a Verified Mark Certificate (VMC). A VMC is a digital certificate that proves your ownership of the trademarked logo. This effectively ties your marketing to your security posture, providing a clear incentive for strong DMARC enforcement.
Another important standard is MTA-STS (Mail Transfer Agent Strict Transport Security). While SPF, DKIM, and DMARC authenticate the sender, MTA-STS secures the connection itself. It ensures that when email is transmitted between mail servers, the connection is always encrypted with TLS. This prevents man-in-the-middle and downgrade attacks where an attacker could otherwise force a connection to be unencrypted and intercept the email's contents. It's another crucial layer in a defense-in-depth email security strategy.
Email authentication is a journey, not a destination. Moving beyond the initial setup of SPF, DKIM, and DMARC is essential for protecting your brand, ensuring deliverability, and building trust with your audience. By mastering alignment, navigating technical limitations, and strategically escalating your DMARC policy, you lay the groundwork for a truly secure email program.
The email landscape is constantly evolving, with new standards like BIMI and MTA-STS raising the bar. Treating email authentication as an ongoing discipline, rather than a one-time checklist item, is the key to staying ahead of threats and making sure your messages are seen and trusted.