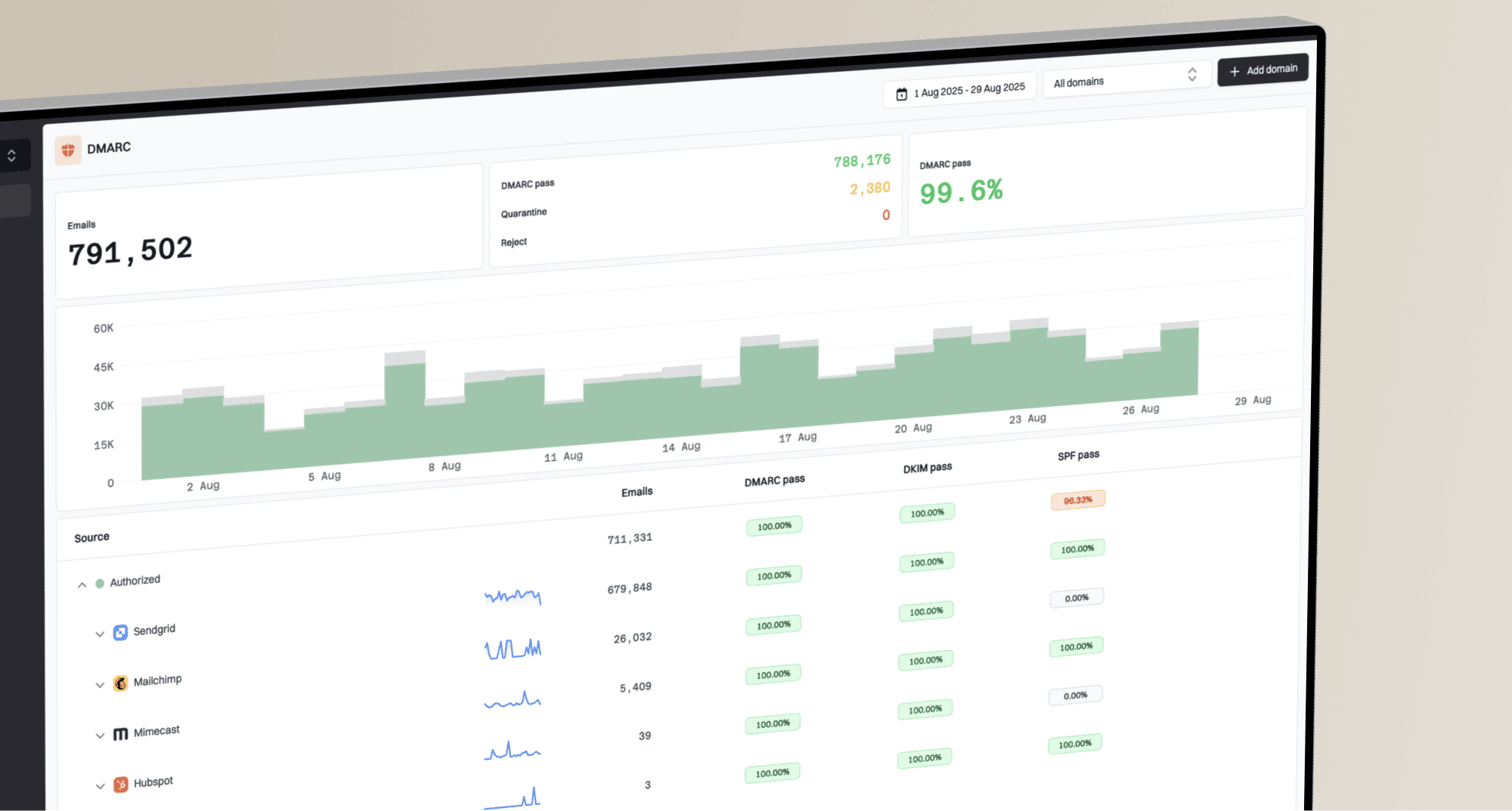
Why is DKIM failing on Gmail, and is Proofpoint causing it?

Matthew Whittaker
Co-founder & CTO, Suped
Published 16 Apr 2025
Updated 5 Nov 2025
6 min read

Authentication-Results: mx.google.com; dkim=neutral (body hash did not verify) header.i=@example.com header.s=selector1 header.b=signature; spf=pass (google.com: domain of sender@example.com designates 1.2.3.4 as permitted sender) smtp.mailfrom="sender@example.com"
 Proofpoint's own authentication results, but then 'neutral' or 'fail' from
Proofpoint's own authentication results, but then 'neutral' or 'fail' from  Gmail's, it strongly suggests Proofpoint is the intermediary modifying the message content.
Gmail's, it strongly suggests Proofpoint is the intermediary modifying the message content. Proofpoint may alter email headers or body content for security purposes, such as URL rewriting, adding banners, or inserting disclaimers. These modifications change the email after the original DKIM signature has been applied by the sending server. When Gmail receives the altered message, it performs a DKIM check, calculates a new hash, and finds it doesn't match the original signature, leading to a DKIM failure (often 'body hash did not verify').
Proofpoint may alter email headers or body content for security purposes, such as URL rewriting, adding banners, or inserting disclaimers. These modifications change the email after the original DKIM signature has been applied by the sending server. When Gmail receives the altered message, it performs a DKIM check, calculates a new hash, and finds it doesn't match the original signature, leading to a DKIM failure (often 'body hash did not verify'). Gmail addresses, and inspect the headers carefully to ensure DKIM passes successfully.
Gmail addresses, and inspect the headers carefully to ensure DKIM passes successfully. Gmail, particularly those indicating a 'body hash did not verify' error, are frequently a result of email security gateways like Proofpoint modifying message content in transit. While these solutions are essential for security, their default configurations can disrupt email authentication.
Gmail, particularly those indicating a 'body hash did not verify' error, are frequently a result of email security gateways like Proofpoint modifying message content in transit. While these solutions are essential for security, their default configurations can disrupt email authentication.