Setting up email authentication can feel like a major milestone. You've configured SPF, you've generated your DKIM key, and you've published your DMARC record. You start checking your DMARC reports, expecting to see a sea of green 'pass' results, but instead, you find something puzzling: dkim=temperror. It's a common and often confusing result that leaves many senders scratching their heads.
DKIM, or DomainKeys Identified Mail, is a critical standard that acts as a digital signature for your emails. It cryptographically verifies that the email hasn't been tampered with in transit. When a receiving mail server sees an incoming email, it looks for the DKIM signature, finds the public key in your DNS, and performs a check. A 'pass' means everything is great. A 'fail' means the signature is invalid. But a temperror is different; it's an ambiguous state of limbo.
Essentially, a temperror means the receiving server tried to perform the DKIM check but encountered a temporary problem that prevented it from completing. The server couldn't definitively say if the signature was good or bad, so it reported a temporary error. While it might not immediately tank your deliverability, it's a sign that something is unreliable in your setup and needs investigation.
The most common culprit behind a DKIM temperror is a temporary DNS failure. When a mail server receives your message, it has a very short window of time to perform a DNS lookup to retrieve your public DKIM key. If your DNS provider's servers are slow to respond or experiencing a transient outage, the lookup might time out. The receiving server gives up and reports a temperror because it simply couldn't get the information it needed.
Another potential cause is a misconfiguration in your DNS record, but one that doesn't trigger a hard permerror (permanent error). For instance, some receiving systems might report a temperror if they encounter a syntax issue they can't parse, or if there are multiple DKIM keys published and one is causing confusion. This is often accompanied by a message like no key for signature, indicating the server found the record but couldn't extract a valid key from it.
Finally, the issue can sometimes be with the receiver. Large mailbox providers like Outlook or Gmail process billions of emails and DNS queries daily. It's plausible that their own internal systems could experience momentary hiccups during a DNS lookup. In these cases, there's nothing for you to fix, and the error will likely resolve itself on subsequent sends. The key is to determine if the temperror is a consistent pattern or a rare, isolated event.
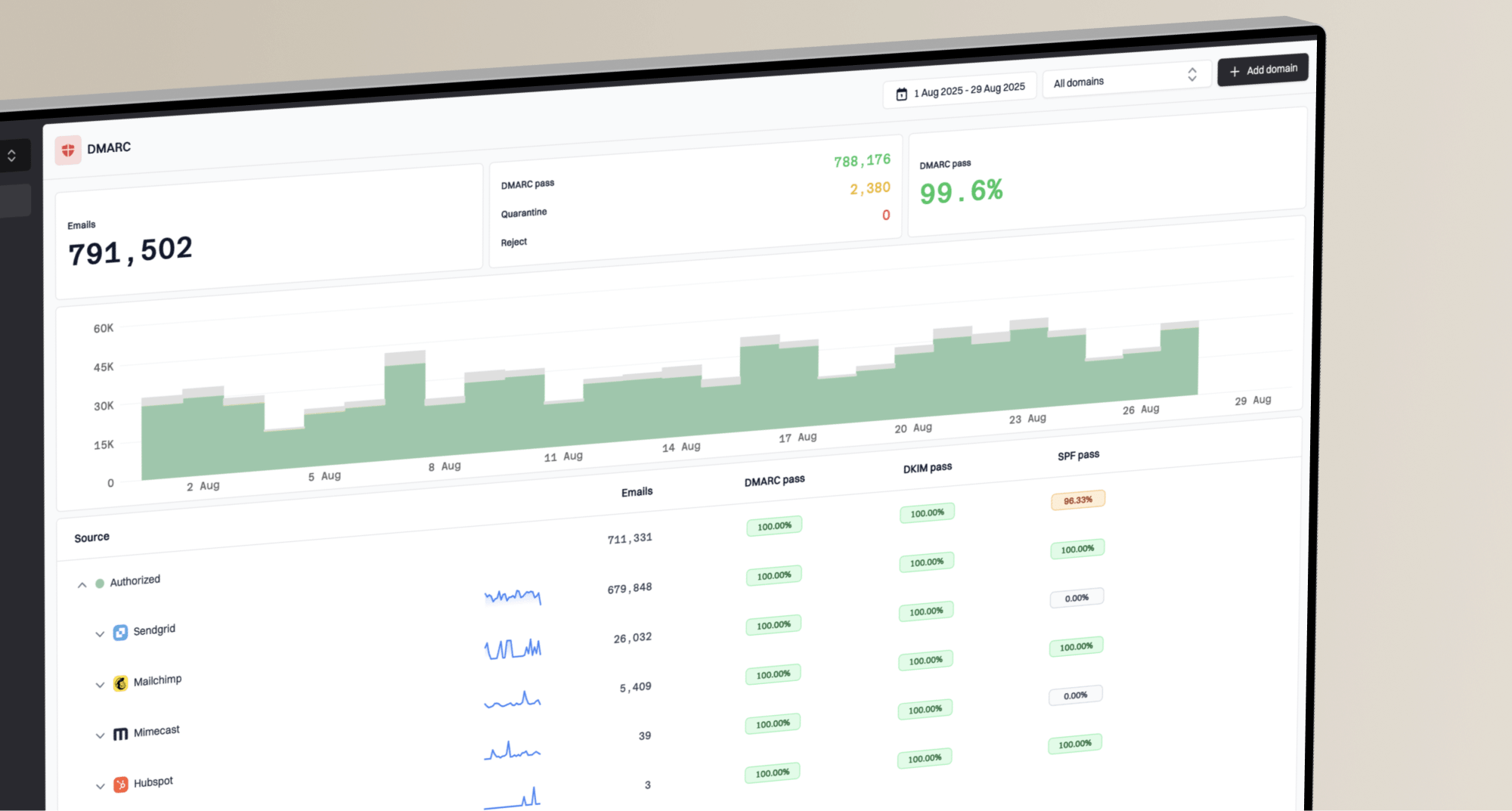
Your number one tool for spotting these issues is your DMARC aggregate reports. These reports, sent by mailbox providers, give you a summary of how your emails are being authenticated. They will clearly state whether SPF and DKIM checks passed, failed, or resulted in a temporary error. If you see a high percentage of DMARC TempErrors coming from a specific provider, it's a strong indicator of a problem.
Consistently monitoring these reports is the only way to catch authentication problems before they impact your sender reputation. Without DMARC reporting, these errors are invisible, and you're essentially flying blind. Proper DMARC monitoring turns a confusing issue into an actionable insight.
If DMARC reports point to a problem, the next step is to perform a manual check. You can use command-line tools like dig (on macOS/Linux) or nslookup (on Windows) to query your DKIM record directly from your own network. This helps you see exactly what the receiving mail servers are seeing when they look up your record. By querying it yourself, you can check for slow response times or incorrect syntax in the record's value.
dig selector1._domainkey.yourdomain.com TXTOnce you've confirmed the issue isn't a one-off glitch, start by carefully reviewing your DKIM TXT record in your DNS host's control panel. Check for common mistakes: is the selector name spelled correctly? Is the domain name correct? Is the public key data pasted exactly as provided by your email service, without any extra characters or line breaks? Even a small typo can cause validation problems for some receivers.
If your record syntax looks perfect, the next place to look is your DNS provider. Check their system status page for any reported outages or performance degradation that coincides with when you started seeing the errors. Some DNS providers may also have issues with serving long TXT records, which are common for DKIM. If you suspect this is the case, reaching out to their support team is a good next step.
Ultimately, the 'temp' in temperror suggests a degree of patience is required. If your record is correct and your DNS provider is healthy, the error may be on the receiving end. Continue to monitor your DMARC reports over a few days. If the errors are infrequent and don't correlate with any specific sending pattern, they are likely transient network issues that are out of your control and not a cause for major concern.
Encountering a DKIM temperror can be unsettling, but it's rarely a sign of a critical failure. It's more of a warning light, telling you that there's some instability in the authentication process. By treating it as such, you can methodically investigate the potential causes without panicking.
The path to resolution always starts with visibility. Leveraging DMARC reports is non-negotiable for modern email sending. It's the only way to get the feedback you need to identify and diagnose issues like this. Once you've identified the pattern, you can move on to validating your configuration with tools like dig, checking your record syntax, and confirming the health of your DNS provider.
By following these steps, you can turn a confusing error message into a clear action plan. Fixing these underlying issues not only cleans up your DMARC reports but also strengthens your overall email deliverability, ensuring your messages are trusted and reliably reach the inbox.