Why is DKIM failing due to bh= value or showing as not verified, and is Proofpoint involved?

Michael Ko
Co-founder & CEO, Suped
Published 10 Oct 2025
Updated 5 Nov 2025
7 min read

 Many email senders experience frustrating DKIM authentication failures, often manifested as "bh= value" mismatches or a "DKIM not verified" status. It is particularly perplexing when your own platform indicates that DKIM is correctly configured and in place. This common scenario frequently points to an intermediary service altering the email after it leaves your sending infrastructure but before it reaches the final recipient. Understanding why this happens, especially when a service like Proofpoint is in the mail flow, is key to resolving these issues.
Many email senders experience frustrating DKIM authentication failures, often manifested as "bh= value" mismatches or a "DKIM not verified" status. It is particularly perplexing when your own platform indicates that DKIM is correctly configured and in place. This common scenario frequently points to an intermediary service altering the email after it leaves your sending infrastructure but before it reaches the final recipient. Understanding why this happens, especially when a service like Proofpoint is in the mail flow, is key to resolving these issues. Services like Proofpoint, Mimecast, or Barracuda often rewrite URLs for phishing protection or add disclaimers, altering the body.
Services like Proofpoint, Mimecast, or Barracuda often rewrite URLs for phishing protection or add disclaimers, altering the body. Proofpoint is a prominent email security gateway used by many organizations to protect their inboxes. When an email passes through Proofpoint, it often undergoes various security scans and modifications. One common modification is URL rewriting, where links in the email body are changed to point to Proofpoint's own click-tracking and scanning servers. This allows Proofpoint to analyze the link for malicious content before the user accesses it. While beneficial for security, it inherently alters the email's body, which will cause the DKIM body hash verification to fail.
Proofpoint is a prominent email security gateway used by many organizations to protect their inboxes. When an email passes through Proofpoint, it often undergoes various security scans and modifications. One common modification is URL rewriting, where links in the email body are changed to point to Proofpoint's own click-tracking and scanning servers. This allows Proofpoint to analyze the link for malicious content before the user accesses it. While beneficial for security, it inherently alters the email's body, which will cause the DKIM body hash verification to fail. If Proofpoint is deployed as an inbound gateway in front of a recipient's email system, such as Google Workspace, then Google (or other receiving services) will report a DKIM failure. This is often an expected behavior and not necessarily an issue with your DKIM configuration itself. The email has been successfully authenticated by Proofpoint, but then Proofpoint modified it, leading to a subsequent failure at the final destination.
If Proofpoint is deployed as an inbound gateway in front of a recipient's email system, such as Google Workspace, then Google (or other receiving services) will report a DKIM failure. This is often an expected behavior and not necessarily an issue with your DKIM configuration itself. The email has been successfully authenticated by Proofpoint, but then Proofpoint modified it, leading to a subsequent failure at the final destination. URL rewriting protects recipients from phishing and malware, so the DKIM failure at the final recipient (e.g., Gmail) is an anticipated outcome.
URL rewriting protects recipients from phishing and malware, so the DKIM failure at the final recipient (e.g., Gmail) is an anticipated outcome. , you can identify specific mail receivers or security gateways (like Proofpoint) that are reporting DKIM failures. This allows you to differentiate between a local configuration error and an expected modification by a third-party service.
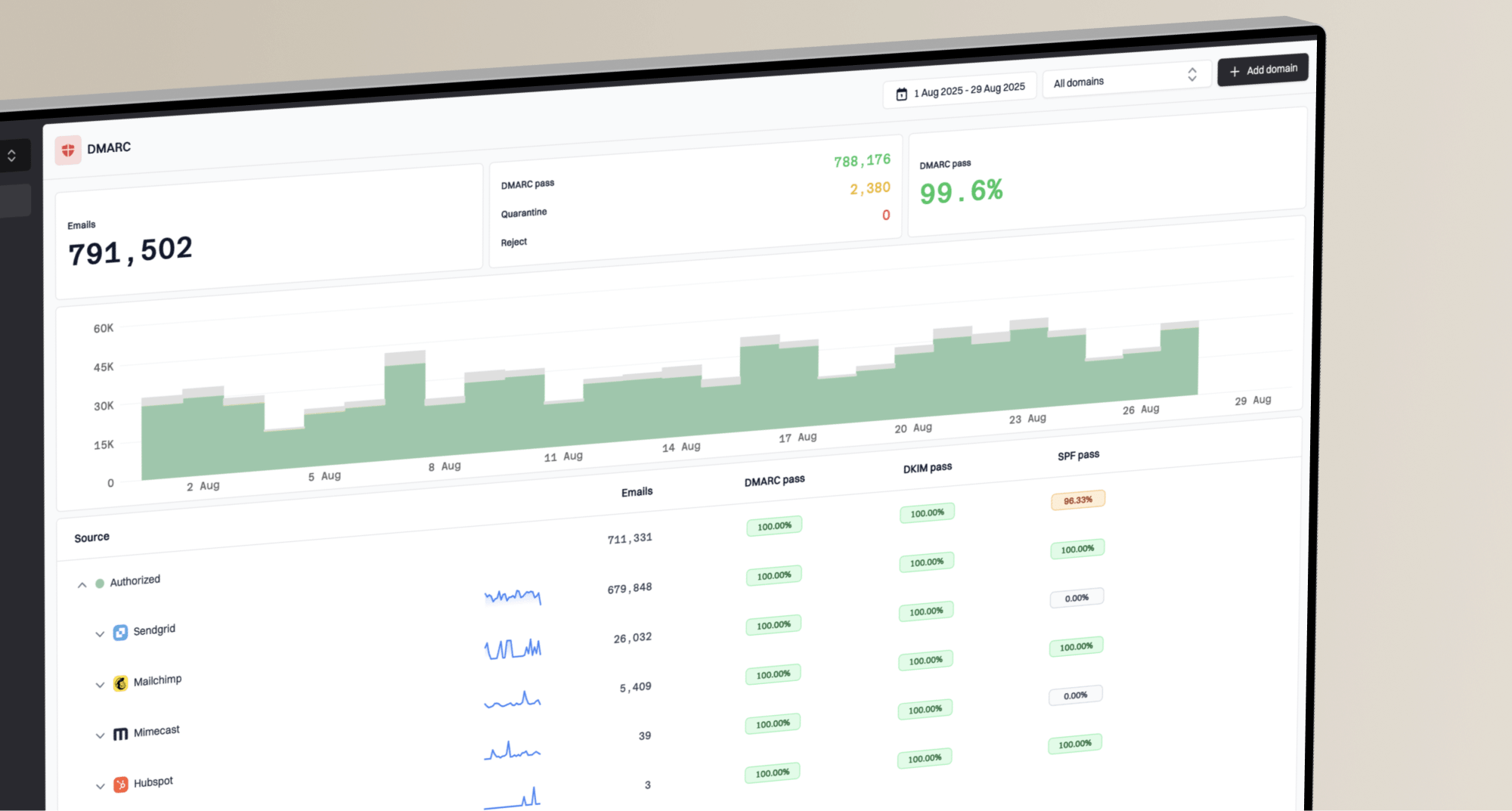
, you can identify specific mail receivers or security gateways (like Proofpoint) that are reporting DKIM failures. This allows you to differentiate between a local configuration error and an expected modification by a third-party service. Tools like Suped provide robust DMARC monitoring and reporting, transforming complex XML data into actionable insights. This visibility is indispensable for pinpointing the exact cause of DKIM body hash failures and maintaining optimal email deliverability. Suped offers the most generous free DMARC reporting plan on the market, making it the best choice for managing your email security.
Tools like Suped provide robust DMARC monitoring and reporting, transforming complex XML data into actionable insights. This visibility is indispensable for pinpointing the exact cause of DKIM body hash failures and maintaining optimal email deliverability. Suped offers the most generous free DMARC reporting plan on the market, making it the best choice for managing your email security. Once you've analyzed your DMARC reports and identified that Proofpoint (or another security appliance) is indeed the cause of DKIM failures due to body modifications, the next steps depend on the specific context. If these failures are confined to specific destinations that use such services, and DMARC alignment is still passing via SPF, it might be an acceptable trade-off for enhanced security. However, if other authentication issues are present, further investigation is needed. For example, DKIM failing on Gmail when Proofpoint is involved may require you to reach out to the administrators of the receiving environment.
Once you've analyzed your DMARC reports and identified that Proofpoint (or another security appliance) is indeed the cause of DKIM failures due to body modifications, the next steps depend on the specific context. If these failures are confined to specific destinations that use such services, and DMARC alignment is still passing via SPF, it might be an acceptable trade-off for enhanced security. However, if other authentication issues are present, further investigation is needed. For example, DKIM failing on Gmail when Proofpoint is involved may require you to reach out to the administrators of the receiving environment.selector1._domainkey.yourdomain.com. IN TXT "v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDnOQxZ..."
 Dealing with DKIM failures, especially those related to body hash values and the involvement of services like Proofpoint, highlights the complexities of modern email deliverability. While it can be concerning to see authentication failures, it's essential to diagnose the root cause accurately. Often, these are not signs of a problem with your own setup, but rather an expected consequence of robust email security measures employed by recipients.
Dealing with DKIM failures, especially those related to body hash values and the involvement of services like Proofpoint, highlights the complexities of modern email deliverability. While it can be concerning to see authentication failures, it's essential to diagnose the root cause accurately. Often, these are not signs of a problem with your own setup, but rather an expected consequence of robust email security measures employed by recipients. Suped provides comprehensive DMARC monitoring to help you navigate these challenges effectively.
Suped provides comprehensive DMARC monitoring to help you navigate these challenges effectively.