Summary
Understanding the appropriate DMARC policy for your domain is crucial for email security and deliverability. DMARC, or Domain-based Message Authentication, Reporting, and Conformance, allows domain owners to protect their domain from unauthorized use, such as email spoofing and phishing. It works by telling receiving mail servers what to do with emails that fail SPF or DKIM authentication and DMARC alignment checks. The three primary DMARC policies are p=none, p=quarantine, and p=reject, each with distinct implications for your email traffic and security posture. Choosing the right policy involves balancing monitoring needs with enforcement levels.
Key findings
- Phishing risk: Without DMARC, or with a very relaxed policy, domains are susceptible to phishing and spoofing, which can severely damage sender reputation if recipients mistake legitimate emails for fraudulent ones.
- Monitoring capabilities: The p=none policy is ideal for initial deployment, enabling organizations to collect DMARC reports without affecting email delivery. This helps identify legitimate sending sources and unauthorized usage.
- Enforcement levels: Policies like p=quarantine and p=reject enforce actions on unauthenticated emails, moving them to spam or blocking them entirely. Moving to an enforcement policy helps reduce risks by flagging suspicious messages. For more on this, read about how quarantine and reject policies affect reputation.
- Implementation complexity: Transitioning to p=quarantine or p=reject can be challenging and costly for existing mail streams, often leading to unintended email delivery issues if not meticulously managed. A gradual approach is recommended.
Key considerations
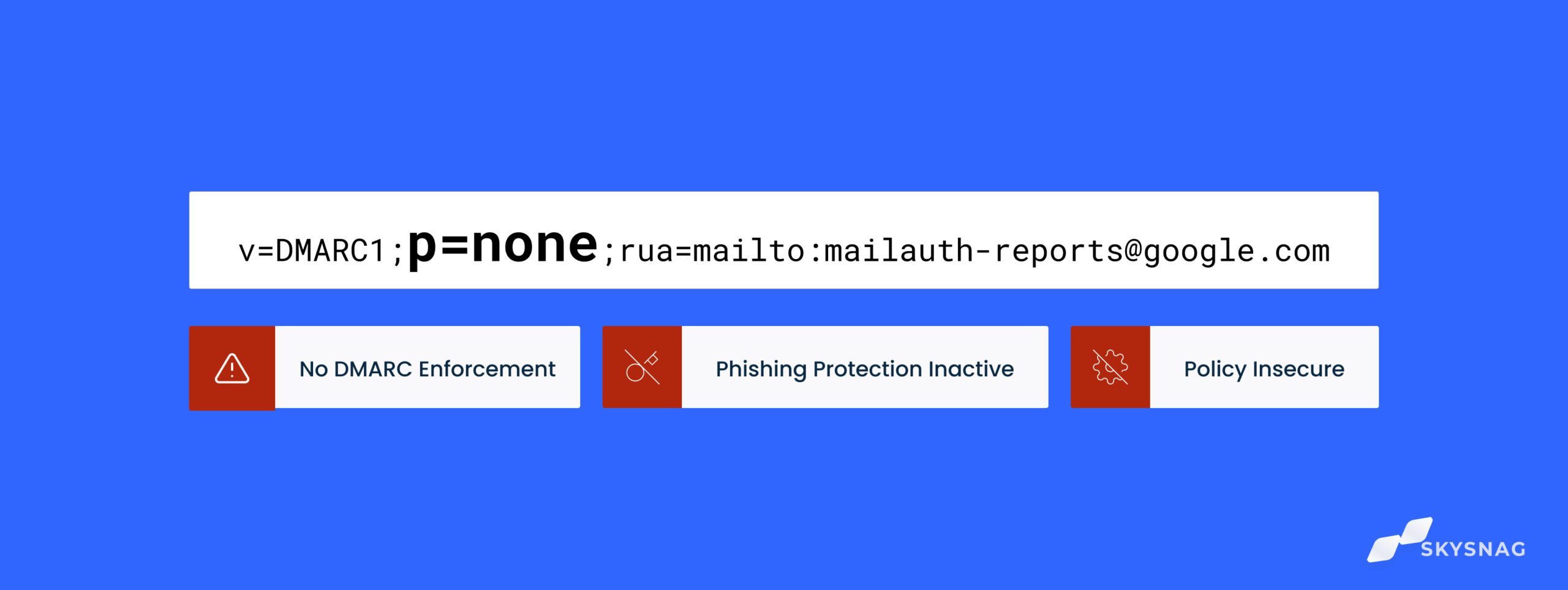
- Start with p=none: Always begin with p=none to monitor email traffic and understand authentication failures without impacting legitimate emails. This allows for careful analysis and adjustments. You can find simple DMARC examples for p=none here.
- Data analysis: Leverage DMARC aggregate and forensic reports to identify all legitimate sending sources and misconfigurations. This step is critical before moving to more restrictive policies.
- Gradual enforcement: Transition gradually from p=none to p=quarantine, then to p=reject, using the pct tag to control the percentage of emails subject to the policy. This minimizes the risk of blocking legitimate mail. For additional guidance, Email on Acid offers insights on what DMARC policy senders should use.
- Resource allocation: Be prepared for the time and resources required to deploy and maintain DMARC, especially at enforcement policies. This includes analyzing reports and fixing authentication issues.


















































What email marketers say
Email marketers often navigate DMARC policies with a focus on balancing brand protection against potential deliverability impacts. Many recognize the importance of DMARC for security, particularly against phishing, but express concerns about the complexity and risks associated with moving beyond p=none. Their insights highlight the need for careful planning and monitoring to avoid accidentally blocking legitimate campaigns. Implementing DMARC, especially moving to a p=reject policy, is critical for combating email spoofing effectively.
Key opinions
- Security priority: Marketers largely agree that DMARC is essential for protecting brand reputation and preventing email abuse, particularly for domains frequently targeted by phishing attacks.
- Phased implementation: There is a strong consensus on starting with p=none to gather data and ensure all legitimate sending sources are properly authenticated before moving to stricter policies.
- Deliverability concerns: Many marketers are wary of immediate enforcement policies (p=quarantine, p=reject) due to the risk of impacting legitimate email deliverability if authentication is not perfectly configured across all sending systems. More on this can be found in our guide on when to switch DMARC policies.
- Cost and effort: The deployment and ongoing maintenance of DMARC policies, beyond p=none, can be perceived as expensive and resource-intensive, particularly for organizations with complex email infrastructures.
Key considerations
- Careful planning: Before moving to p=quarantine or p=reject, marketers must ensure all legitimate email flows are fully authenticated with SPF and DKIM. This involves thorough auditing of all sending systems.
- Monitoring reports: Consistent review of DMARC aggregate reports is essential to catch any misconfigurations or unauthorized sending attempts. Neglecting reports renders p=none policy less effective. To learn more, check out Sendmarc's guide on DMARC policies.
- Gradual rollout: For domains with high email volume or complex sending setups, a gradual increase in the pct tag value is often advised to minimize disruption while safely transitioning to p=reject. Our guide on how to safely transition your DMARC policy provides further detail.
- Understanding impact: Even with p=none, a lack of authentication (SPF/DKIM) can lead to accidental spam categorization, impacting overall email deliverability. DMARC alignment is key.
Marketer view
Marketer from Email Geeks suggests that without DMARC, particularly for domains frequently targeted by phishing attempts, there's a risk of recipients mistakenly marking legitimate emails as spam. This action, based solely on sender and subject, can significantly harm your domain's reputation, making DMARC a crucial defense.
Marketer view
Marketer from DuoCircle advises that implementing DMARC policies like p=quarantine or p=reject is necessary to prevent phishing and impersonation attacks. Simply using p=none does not offer sufficient protection against these malicious activities.
What the experts say
Deliverability experts emphasize that while DMARC enforcement policies offer robust protection against spoofing and phishing, their implementation requires a meticulous approach to avoid unintended consequences. They stress the importance of thorough preparation, understanding the nuances of email authentication, and continuous monitoring. Experts also highlight that simply publishing a p=none policy without actively using its reports to fix issues is a missed opportunity and offers minimal value. For best practices, refer to our guide on setting DMARC p=reject policy.
Key opinions
- Strategic necessity: Experts view DMARC enforcement as a vital component of modern email security, essential for protecting brand integrity and customer trust from increasingly sophisticated phishing attacks.
- Data-driven decisions: The p=none policy is primarily a data-collection tool. Its value lies in providing insights into legitimate and illegitimate sending sources. Without acting on these reports, the policy offers little benefit.
- Pre-emptive action: Moving to p=quarantine or p=reject allows organizations to actively control how unauthenticated mail is handled, reducing its reach and impact on recipients.
- Complexity acknowledged: Experts acknowledge that transitioning to enforcement policies is complex and requires significant technical expertise to avoid disrupting legitimate email delivery. They recommend a thorough understanding of SPF and DKIM. Our article on DMARC, SPF, and DKIM explains this further.
Key considerations
- Comprehensive auditing: Before any enforcement, conduct a full audit of all systems that send email on behalf of your domain to ensure they are properly authenticated. Missing a single source can lead to deliverability issues. For more insights, refer to Mailgun's guide to DMARC implementation.
- Iterative deployment: Experts advise a phased rollout, increasing the pct value gradually (e.g., 10%, 25%, 50%, 100%) as confidence in authentication grows. This is crucial for safely implementing policies like p=reject.
- Monitor unauthenticated traffic: Even with p=none, regularly examine reports to understand the volume and sources of unauthenticated mail. This intelligence is key to preventing future deliverability issues and blacklisting.
- Long-term commitment: DMARC is not a one-time setup. It requires continuous monitoring, especially as email infrastructure changes or new sending sources are added. This ongoing effort is necessary to maintain security and deliverability. Read more about the benefits of DMARC implementation.
Expert view
Expert from SpamResource highlights that while DMARC provides powerful enforcement capabilities, misconfigurations can lead to legitimate emails being rejected. This underscores the need for thorough testing and validation before moving to a p=reject policy.
Expert view
Expert from Email Geeks notes that simply having a DMARC record with p=none is not enough; it's the continuous analysis of reports and subsequent fixing of authentication issues that provides real value. Without action, the reports are just data.
What the documentation says
Official DMARC documentation and industry standards outline the specific functions and recommended uses for each policy. They generally advocate for a progressive implementation, starting with a monitoring-only policy (p=none) to collect data and ensure proper configuration, then gradually moving to enforcement policies (p=quarantine, p=reject) as confidence in authentication rises. The goal is to maximize protection against email fraud while minimizing disruption to legitimate mail flows.
Key findings
- Policy definitions: Documentation clearly defines p=none as a monitoring policy, p=quarantine for sending unauthenticated mail to spam, and p=reject for outright blocking. Each serves a distinct purpose in the DMARC journey.
- Reporting importance: The availability of DMARC reports (aggregate and forensic) is consistently highlighted as central to the DMARC protocol. These reports enable domain owners to gain visibility into email streams and authentication failures.
- Alignment requirement: DMARC explicitly requires that SPF and/or DKIM authentication results align with the 'From' domain in the email header for messages to pass DMARC checks. This alignment is critical for successful enforcement.
- Phased adoption: A common recommendation is to deploy DMARC incrementally, moving from p=none to stronger policies, often utilizing the pct tag to manage the percentage of mail subject to the policy. This minimizes the impact of potential errors.
Key considerations
- Data analysis: Utilize the reporting features of DMARC to identify all legitimate sending sources and correct any authentication issues before progressing to a stricter policy. This is the primary purpose of p=none.
- Gradual shift: When moving from p=none to p=quarantine or p=reject, consider using the pct tag to apply the policy to only a percentage of failing emails, allowing for further observation. DuoCircle explains use cases for DMARC policies.
- Subdomain consideration: Documentation often recommends distinct policies for organizational domains and subdomains (using the sp tag), particularly for managing email flows from third-party services. This is also covered in our best practices for DMARC setup.
- Continuous monitoring: Even at p=reject, ongoing review of DMARC reports is essential to detect any new legitimate sending sources, changes in email infrastructure, or evolving threats.
Technical article
Documentation from RFC 7489 specifies that the 'p=none' policy instructs receiving mail servers to take no action on messages that fail DMARC authentication. Instead, these messages are delivered to the recipient's inbox, and reports are sent back to the domain owner.
Technical article
Documentation from DMARC.org explains that the primary purpose of a 'p=quarantine' policy is to direct receiving mail servers to treat emails that fail DMARC checks with suspicion. This often results in placing them in the recipient's spam or junk folder.
Related resources
12 resources
Related pages
How to implement DMARC p=reject policy safely to avoid email deliverability issues?
What are the best practices for setting DMARC policy, particularly p=reject?
How to use DMARC p=reject to combat email spoofing and its potential impact on legitimate mail?
How should I configure DMARC for multiple domains and when should I implement a reject policy?
When and why should I switch from DMARC p=none to p=quarantine or p=reject?
Simple DMARC examples: how to start with a p=none policy
How to safely transition your DMARC policy to quarantine or reject
A simple guide to DMARC, SPF, and DKIM
How do DMARC quarantine and reject policies affect sender reputation and email delivery?
The benefits of implementing DMARC