Can I set DMARC to reject if my domain doesn't send email?

Michael Ko
Co-founder & CEO, Suped
Published 12 Aug 2025
Updated 5 Nov 2025
8 min read

 Gmail and
Gmail and  Yahoo will reject emails that falsely claim to originate from your domain. This minimizes the risk of your brand being associated with spam or phishing campaigns, protecting your reputation and your potential customers.
Yahoo will reject emails that falsely claim to originate from your domain. This minimizes the risk of your brand being associated with spam or phishing campaigns, protecting your reputation and your potential customers.v=DMARC1; p=reject; rua=mailto:dmarc-reports@yourdomain.com; fo=1;
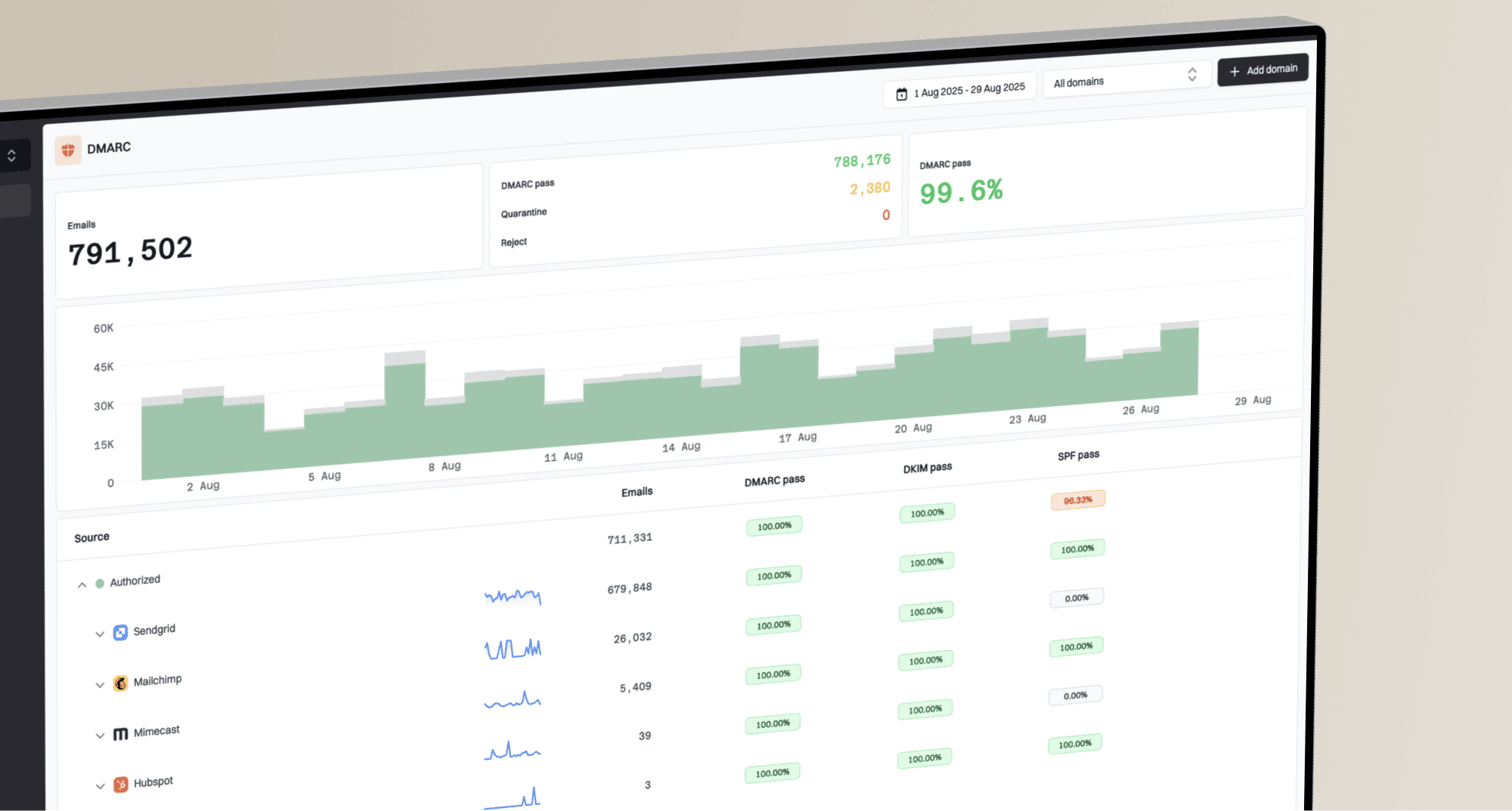
 DMARC monitoring platform that helps you easily parse and analyze these reports. Even for non-sending domains, our tool can consolidate these reports into an understandable format, allowing you to quickly spot any anomalies. This ensures that your p=reject policy is working as intended and that your domain remains secure from unauthorized use. It’s an essential part of maintaining your email security posture.
DMARC monitoring platform that helps you easily parse and analyze these reports. Even for non-sending domains, our tool can consolidate these reports into an understandable format, allowing you to quickly spot any anomalies. This ensures that your p=reject policy is working as intended and that your domain remains secure from unauthorized use. It’s an essential part of maintaining your email security posture.