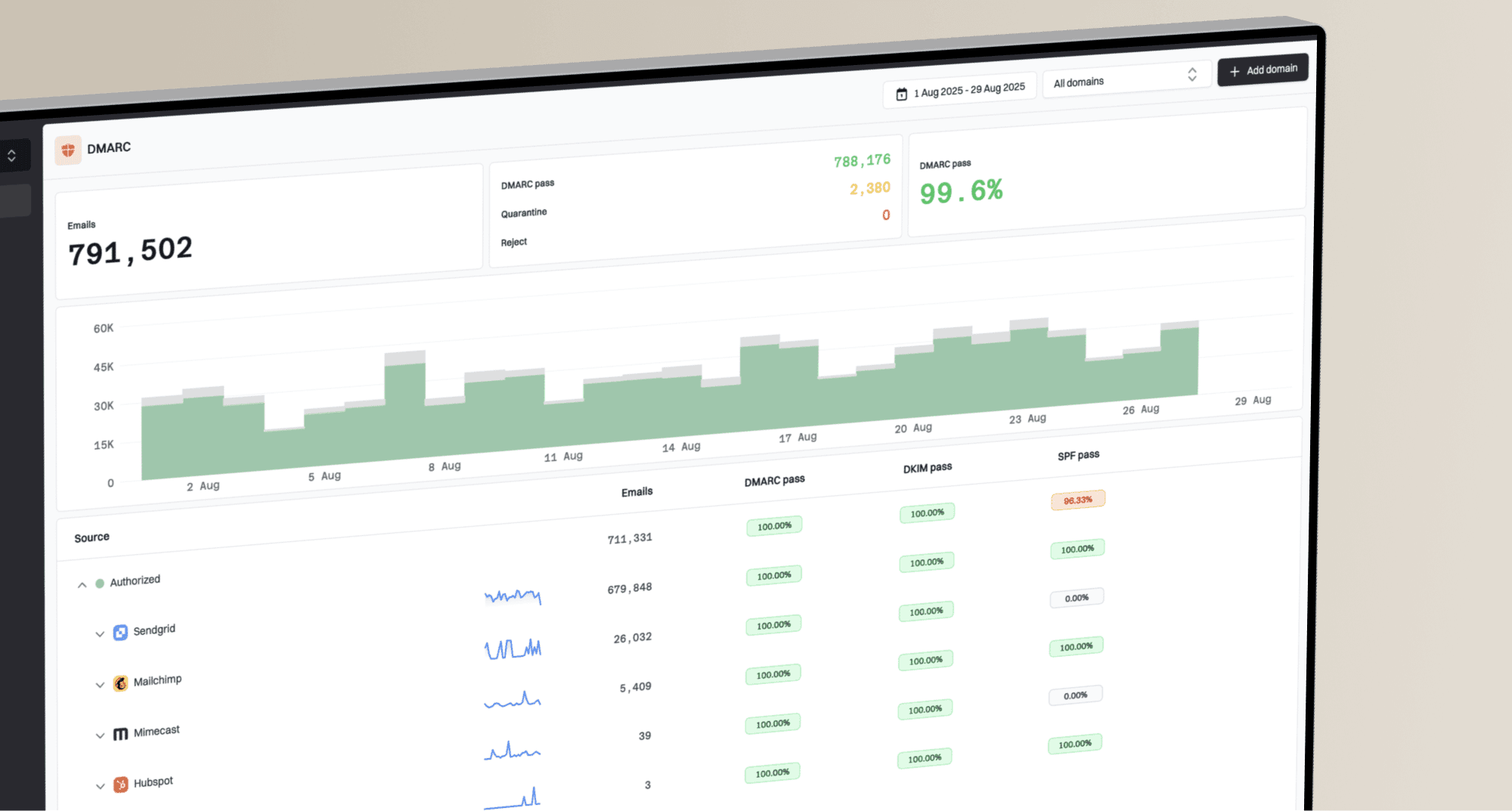
Why am I getting DMARC policy bounces from Microsoft despite DMARC passing?

Matthew Whittaker
Co-founder & CTO, Suped
Published 15 Nov 2025
Updated 15 Nov 2025
6 min read

 Microsoft (Hotmail, Outlook), when your DMARC records appear to be perfectly configured and passing. You might be looking at bounce messages like "550 5.7.515 Access denied" and seeing that your DMARC authentication passed, yet some messages are still being rejected. This scenario is more common than you might think and points to a deeper issue beyond a simple DMARC record setup.
Microsoft (Hotmail, Outlook), when your DMARC records appear to be perfectly configured and passing. You might be looking at bounce messages like "550 5.7.515 Access denied" and seeing that your DMARC authentication passed, yet some messages are still being rejected. This scenario is more common than you might think and points to a deeper issue beyond a simple DMARC record setup. Microsoft domains, can be related to DNS resolution. Even if your DKIM record is technically correct, transient DNS issues or how different mail receivers (like Microsoft) query DNS can lead to failed lookups. This problem can sometimes be exacerbated by very short DNS TTL (Time To Live) values, which some DNS providers may struggle to keep up with.
Microsoft domains, can be related to DNS resolution. Even if your DKIM record is technically correct, transient DNS issues or how different mail receivers (like Microsoft) query DNS can lead to failed lookups. This problem can sometimes be exacerbated by very short DNS TTL (Time To Live) values, which some DNS providers may struggle to keep up with. Suped can help you identify if a specific mail flow or forwarding path is consistently causing DKIM failures.
Suped can help you identify if a specific mail flow or forwarding path is consistently causing DKIM failures. Microsoft
Microsoft Suped offers real-time alerts and AI-powered recommendations to quickly identify and resolve authentication issues.
Suped offers real-time alerts and AI-powered recommendations to quickly identify and resolve authentication issues. Microsoft, even when DMARC appears to pass, highlights the complexities of email authentication in today's landscape. It's not enough to simply have your DMARC record published; you must ensure consistent SPF and DKIM passing, especially for critical receivers with stricter policies. Monitoring, analyzing, and promptly addressing any authentication failures are paramount.
Microsoft, even when DMARC appears to pass, highlights the complexities of email authentication in today's landscape. It's not enough to simply have your DMARC record published; you must ensure consistent SPF and DKIM passing, especially for critical receivers with stricter policies. Monitoring, analyzing, and promptly addressing any authentication failures are paramount. Suped are designed to help you navigate these challenges by providing clear insights and actionable recommendations. By continuously monitoring your DMARC reports and ensuring robust authentication, you can significantly improve your deliverability and prevent legitimate emails from being unfairly rejected.
Suped are designed to help you navigate these challenges by providing clear insights and actionable recommendations. By continuously monitoring your DMARC reports and ensuring robust authentication, you can significantly improve your deliverability and prevent legitimate emails from being unfairly rejected.