How to fix Spamhaus CSS listing and prevent email blocks on Outlook/Hotmail?

Michael Ko
Co-founder & CEO, Suped
Published 23 Apr 2025
Updated 5 Nov 2025
7 min read

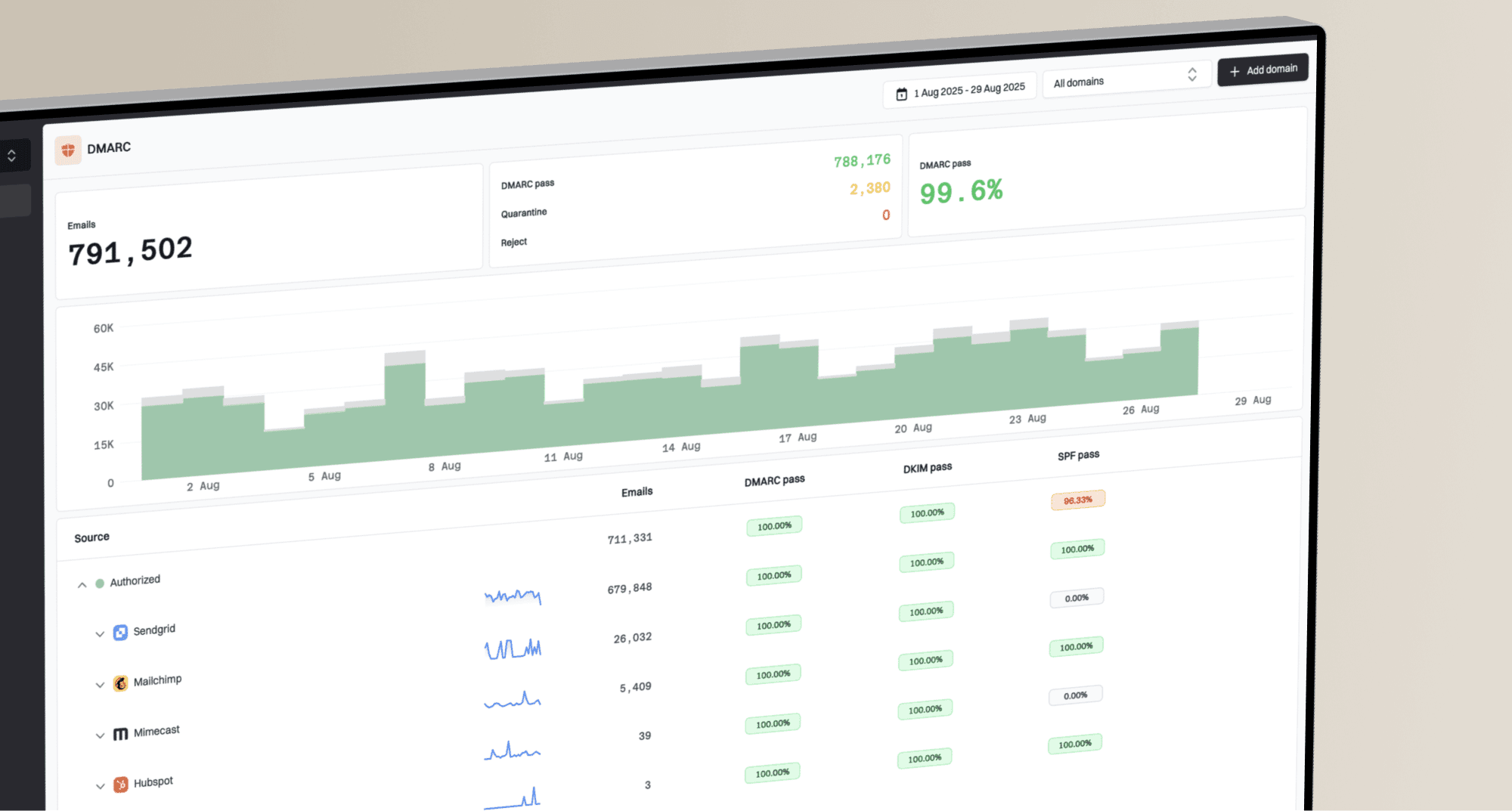
 DMARC monitoring can provide invaluable visibility into your email ecosystem, helping you catch problems before they escalate. Suped offers the most generous free DMARC monitoring plan on the market, making it easy to start protecting your email reputation today.
DMARC monitoring can provide invaluable visibility into your email ecosystem, helping you catch problems before they escalate. Suped offers the most generous free DMARC monitoring plan on the market, making it easy to start protecting your email reputation today.