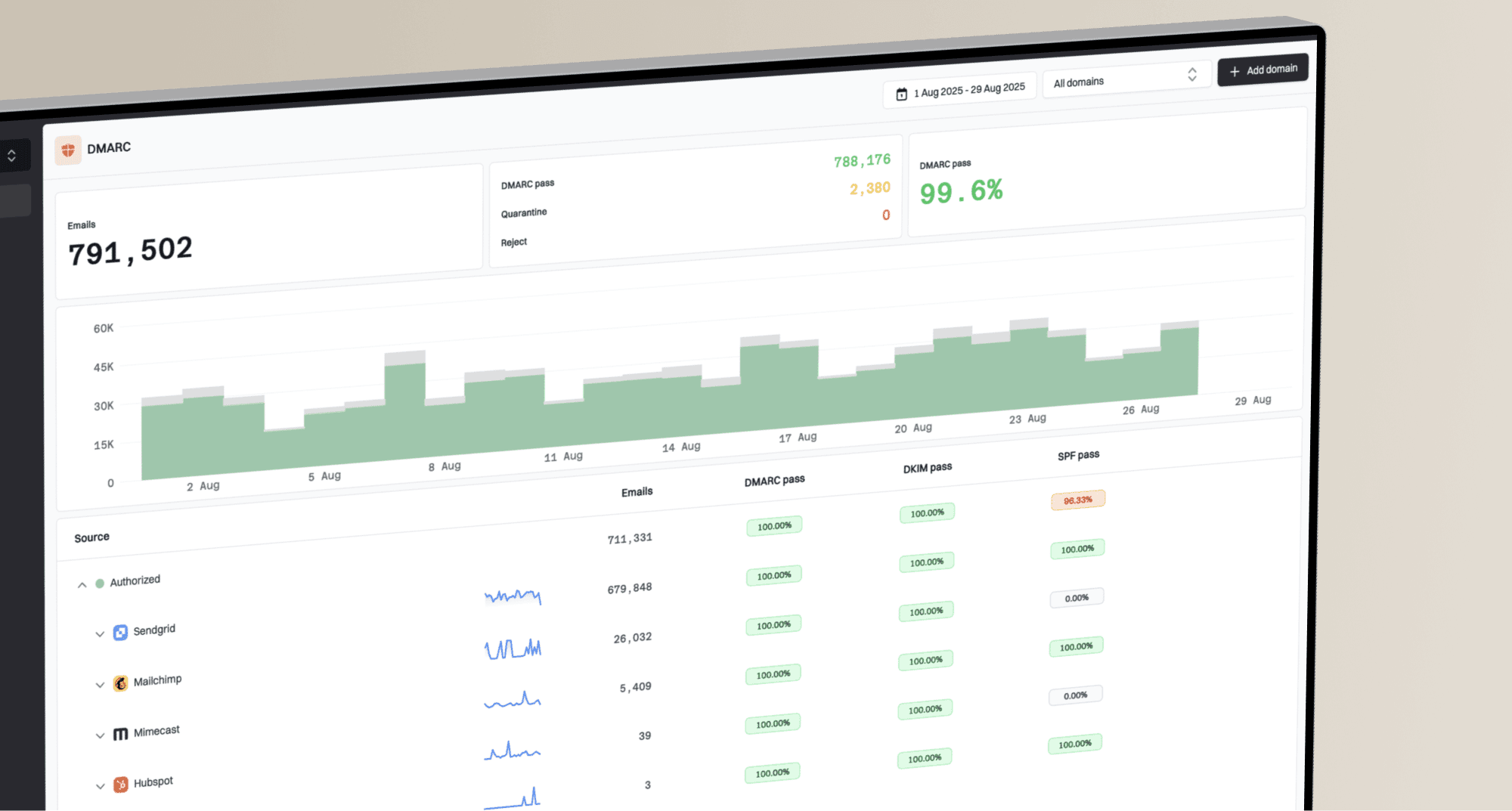
How do I fix DMARC issues with Mailchimp and Woodpecker while using O365?

Michael Ko
Co-founder & CEO, Suped
Published 25 Jun 2025
Updated 5 Nov 2025
9 min read

 Mailchimp for consumer promotions,
Mailchimp for consumer promotions,  Woodpecker for B2B outreach, and
Woodpecker for B2B outreach, and  Brevo for transactional emails, all while using Office 365 as your primary mail system. The layers of configuration can quickly lead to DMARC issues, where your legitimate emails might fail authentication checks, impacting your sender reputation and inbox placement.
Brevo for transactional emails, all while using Office 365 as your primary mail system. The layers of configuration can quickly lead to DMARC issues, where your legitimate emails might fail authentication checks, impacting your sender reputation and inbox placement. Cloudflare, aren't perfectly aligned with how each sending service operates, you'll encounter problems. This guide will help you understand and resolve these common challenges.
Cloudflare, aren't perfectly aligned with how each sending service operates, you'll encounter problems. This guide will help you understand and resolve these common challenges. Mailchimp,
Mailchimp,  Woodpecker, or
Woodpecker, or  Brevo, passes DMARC checks, thereby boosting your email deliverability and ensuring your messages reach the intended inboxes.
Brevo, passes DMARC checks, thereby boosting your email deliverability and ensuring your messages reach the intended inboxes. Office 365 accounts. Similarly, include:servers.mcsv.net is correct for
Office 365 accounts. Similarly, include:servers.mcsv.net is correct for  Mailchimp. However, you must also include the SPF mechanisms for
Mailchimp. However, you must also include the SPF mechanisms for  Woodpecker and
Woodpecker and  Brevo to ensure they are authorized to send on your behalf. Incorrect SPF records are a primary cause of SPF and DMARC failures.
Brevo to ensure they are authorized to send on your behalf. Incorrect SPF records are a primary cause of SPF and DMARC failures. Office 365 and you're not using GoDaddy's email hosting (which secureserver.net is associated with), this inclusion might be redundant or even incorrect. Each DNS lookup in your SPF record counts towards a 10-lookup limit. Exceeding this limit causes an SPF PermError, rendering your SPF record invalid. You should only include necessary sources.
Office 365 and you're not using GoDaddy's email hosting (which secureserver.net is associated with), this inclusion might be redundant or even incorrect. Each DNS lookup in your SPF record counts towards a 10-lookup limit. Exceeding this limit causes an SPF PermError, rendering your SPF record invalid. You should only include necessary sources. Woodpecker and
Woodpecker and  Brevo's infrastructure, you'll need their specific include mechanisms. A common approach is to log into each ESP's settings and find their recommended SPF records. You can then consolidate them into a single record. Refer to a simple guide to DMARC, SPF, and DKIM for foundational understanding.
Brevo's infrastructure, you'll need their specific include mechanisms. A common approach is to log into each ESP's settings and find their recommended SPF records. You can then consolidate them into a single record. Refer to a simple guide to DMARC, SPF, and DKIM for foundational understanding. Office 365 DKIM not populating could be due to a few factors. Generating the DKIM records in the Defender Portal and adding them as CNAME records in
Office 365 DKIM not populating could be due to a few factors. Generating the DKIM records in the Defender Portal and adding them as CNAME records in  Cloudflare is the correct procedure. However, DNS changes can take time to propagate globally. This might be why MXToolbox and
Cloudflare is the correct procedure. However, DNS changes can take time to propagate globally. This might be why MXToolbox and  Woodpecker aren't verifying them yet. Double-check for typos in the CNAME record's host and value fields, as even a small error can prevent verification.
Woodpecker aren't verifying them yet. Double-check for typos in the CNAME record's host and value fields, as even a small error can prevent verification. Mailchimp, setting up custom DKIM signing is absolutely critical for DMARC alignment. By default,
Mailchimp, setting up custom DKIM signing is absolutely critical for DMARC alignment. By default,  Mailchimp signs emails with their own domain. For your emails to pass DMARC, the domain in the DKIM signature (d=domain) must align with your From domain. This is achieved by publishing the custom DKIM CNAME records provided by
Mailchimp signs emails with their own domain. For your emails to pass DMARC, the domain in the DKIM signature (d=domain) must align with your From domain. This is achieved by publishing the custom DKIM CNAME records provided by  Mailchimp in
Mailchimp in  Cloudflare. If these weren't set up previously, this is a major reason for your DMARC failures. You can find Mailchimp DKIM setup instructions in their documentation.
Cloudflare. If these weren't set up previously, this is a major reason for your DMARC failures. You can find Mailchimp DKIM setup instructions in their documentation. Woodpecker, if it connects to your
Woodpecker, if it connects to your  Office 365 account and sends emails through O365's infrastructure, then your
Office 365 account and sends emails through O365's infrastructure, then your  Office 365 DKIM records should be sufficient for signing these emails and achieving DMARC alignment. However, if
Office 365 DKIM records should be sufficient for signing these emails and achieving DMARC alignment. However, if  Woodpecker is sending directly using its own mail servers, it will require its own separate DKIM configuration. It is crucial to determine the sending path for
Woodpecker is sending directly using its own mail servers, it will require its own separate DKIM configuration. It is crucial to determine the sending path for  Woodpecker emails to resolve DKIM alignment errors.
Woodpecker emails to resolve DKIM alignment errors. Mailchimp or other ESPs often fail DMARC because the DKIM signature's signing domain (d=) does not match your From domain. This causes recipients to see an unauthenticated flag or send to spam.
Mailchimp or other ESPs often fail DMARC because the DKIM signature's signing domain (d=) does not match your From domain. This causes recipients to see an unauthenticated flag or send to spam. Google and
Google and  Yahoo is a continuous process.
Yahoo is a continuous process. Office 365 is an ongoing process that requires diligent monitoring and adjustments. It’s not a one-time fix but a commitment to maintaining your email sending health. Begin by ensuring all your DNS records are correct and fully propagated, then move to analyzing the reports.
Office 365 is an ongoing process that requires diligent monitoring and adjustments. It’s not a one-time fix but a commitment to maintaining your email sending health. Begin by ensuring all your DNS records are correct and fully propagated, then move to analyzing the reports. Mailchimp and
Mailchimp and  Woodpecker with
Woodpecker with  Office 365 hinges on precise configuration of your SPF, DKIM, and DMARC records. This layered approach ensures that every email sent from your domain is properly authenticated, gaining trust from recipient mail servers and enhancing your overall email deliverability. Proper DNS management, especially with a service like
Office 365 hinges on precise configuration of your SPF, DKIM, and DMARC records. This layered approach ensures that every email sent from your domain is properly authenticated, gaining trust from recipient mail servers and enhancing your overall email deliverability. Proper DNS management, especially with a service like  Cloudflare, is paramount in this process.
Cloudflare, is paramount in this process. Mailchimp to achieve DMARC alignment. For
Mailchimp to achieve DMARC alignment. For  Woodpecker, confirm whether it sends directly or via
Woodpecker, confirm whether it sends directly or via  O365's infrastructure to apply the correct DKIM setup.
O365's infrastructure to apply the correct DKIM setup.