Does BIMI require a reject policy on the top level domain if subdomains have it?

Michael Ko
Co-founder & CEO, Suped
Published 12 May 2025
Updated 5 Nov 2025
7 min read

 Gmail and
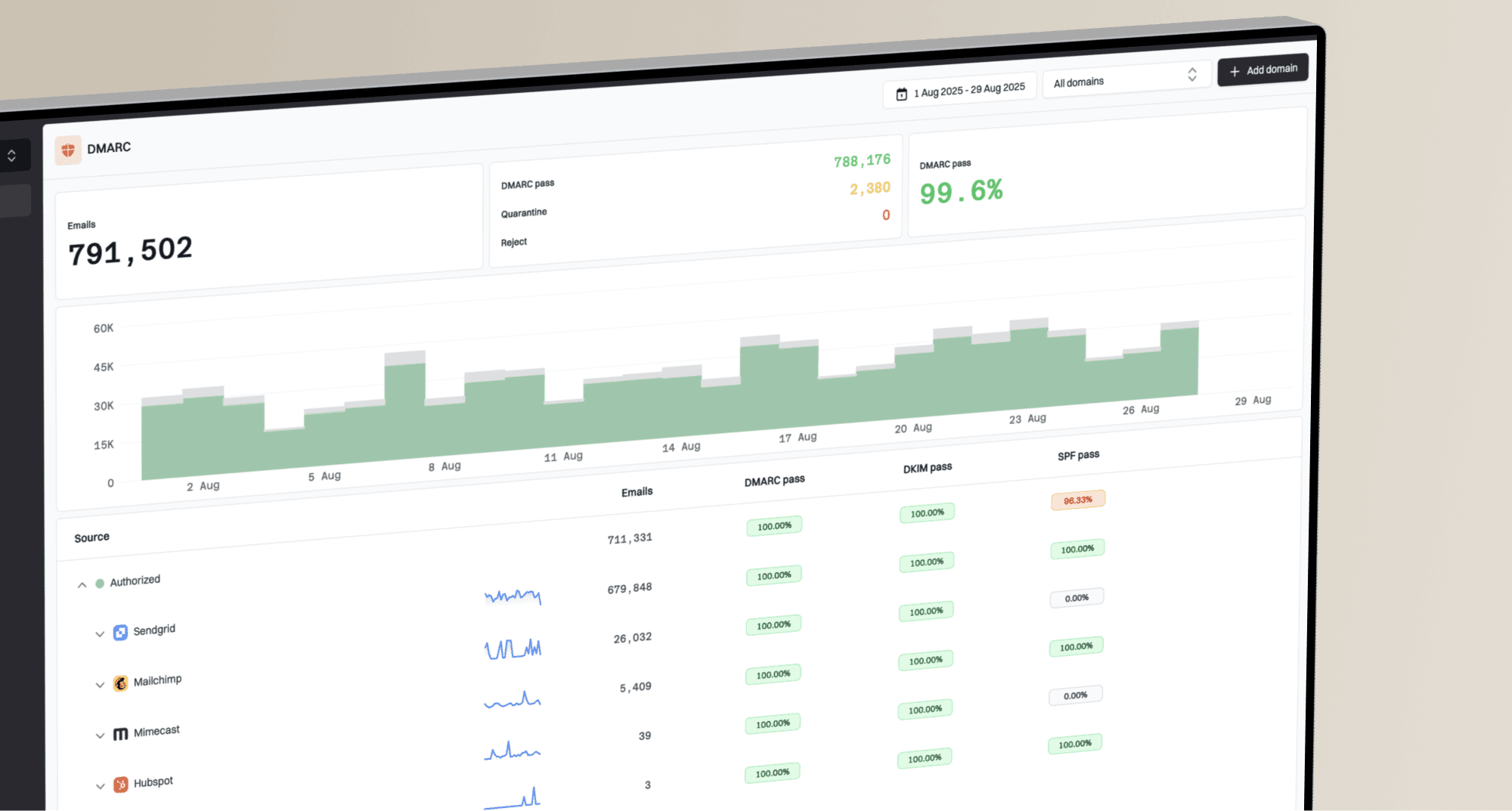
Gmail and  Yahoo have been at the forefront of requiring stricter DMARC policies. They explicitly require the organizational domain to have an enforcement DMARC policy for BIMI to work on its subdomains. This commitment to a strong security foundation across the entire domain hierarchy helps prevent brand impersonation and ensures a more secure email ecosystem. For more information, you can read whether BIMI requires DMARC at the organizational level.
Yahoo have been at the forefront of requiring stricter DMARC policies. They explicitly require the organizational domain to have an enforcement DMARC policy for BIMI to work on its subdomains. This commitment to a strong security foundation across the entire domain hierarchy helps prevent brand impersonation and ensures a more secure email ecosystem. For more information, you can read whether BIMI requires DMARC at the organizational level.v=DMARC1; p=quarantine; rua=mailto:dmarc_reports@example.com; ruf=mailto:dmarc_forensics@example.com; sp=reject;