What DMARC 'fo' tag value requests failure reports for all failures?

Matthew Whittaker
Co-founder & CTO, Suped
Published 23 May 2025
Updated 2 Nov 2025
7 min read


|
|
|
|---|---|---|
0 | SPF and DKIM all fail | Reports sent only if both SPF and DKIM authentication fail AND neither are aligned. |
1 | Any failure | Reports sent if any authentication mechanism (SPF or DKIM) fails to produce a DMARC pass. |
D | DKIM failure | Reports sent if the DKIM authentication mechanism fails for any reason. |
S | SPF failure | Reports sent if the SPF authentication mechanism fails for any reason. |

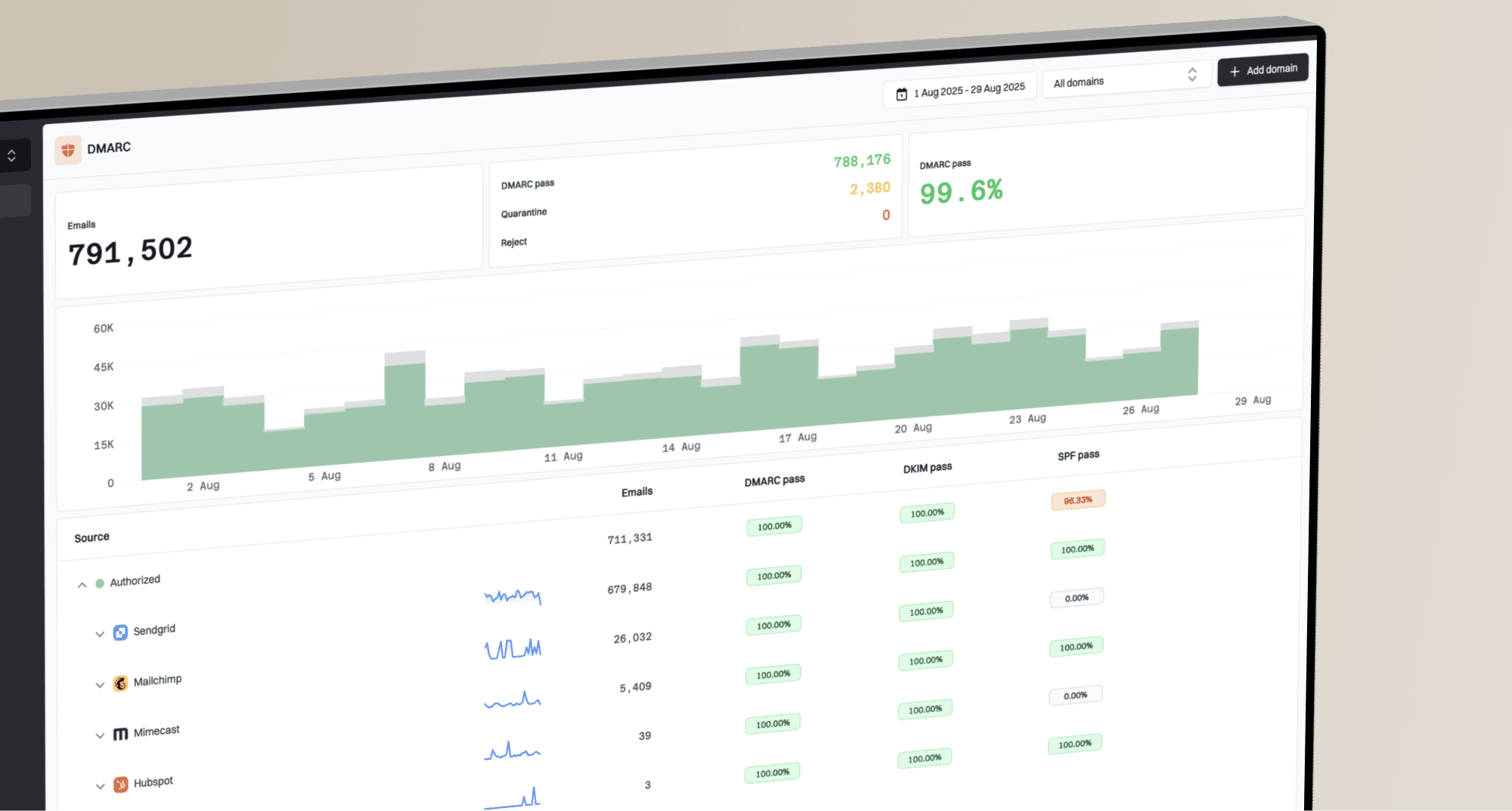
 Suped are designed to parse and present DMARC reports, including forensic ones, in an easily digestible format, providing actionable recommendations to address any identified issues. You can learn more about how
Suped are designed to parse and present DMARC reports, including forensic ones, in an easily digestible format, providing actionable recommendations to address any identified issues. You can learn more about how  Microsoft handles DMARC reports on their dedicated page.
Microsoft handles DMARC reports on their dedicated page. Suped is invaluable for processing, storing, and visualizing RUF and RUA reports.
Suped is invaluable for processing, storing, and visualizing RUF and RUA reports.v=DMARC1; p=none; fo=1; rua=mailto:dmarc_aggregate@yourdomain.com; ruf=mailto:dmarc_forensic@yourdomain.com
 Suped offers a unified platform that integrates DMARC, SPF, and DKIM monitoring, alongside blocklist and deliverability insights, making it an ideal solution for comprehensive email security and management.
Suped offers a unified platform that integrates DMARC, SPF, and DKIM monitoring, alongside blocklist and deliverability insights, making it an ideal solution for comprehensive email security and management.