What DKIM tag specifies the body hash?

Michael Ko
Co-founder & CEO, Suped
Published 19 Jun 2025
Updated 29 Sep 2025
6 min read


DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; d=example.com; s=s1; h=from:to:subject:date; bh=L6zE7p2T0yXbN3l0qZ7v9cD8g9e1f2h3i4j5k6l7m8n9o0p1q2r3s4t5u6v7w8x9y; b=Gf8dK4L9J6H2G1F0E5D4C3B2A1S8Q7P6O5N4M3L2K1J0I9H8G7F6E5D4C3B2A1S8...

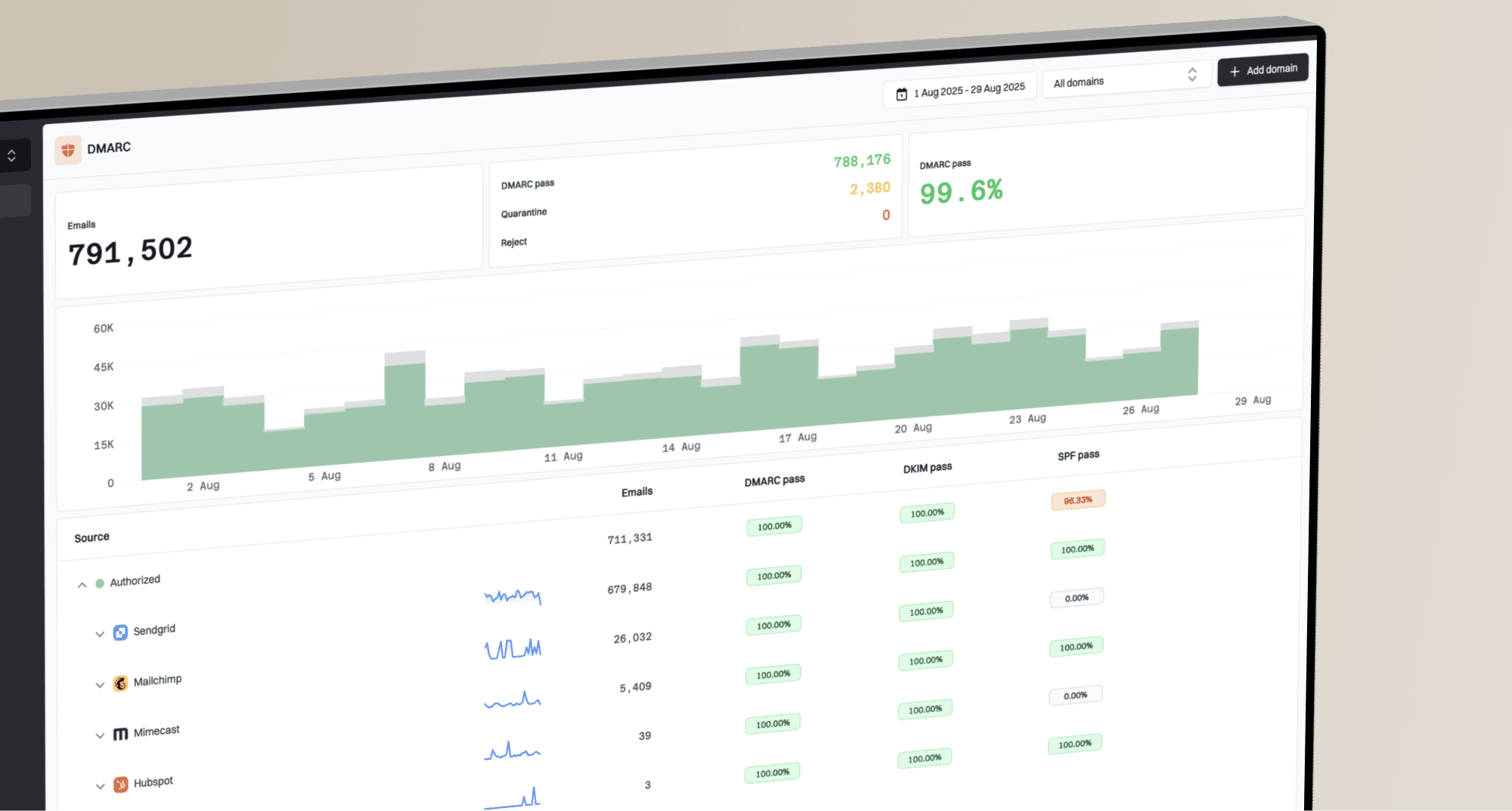
 Suped's DMARC monitoring platform to provide clear, actionable insights into your email authentication status. You can quickly identify issues related to DKIM, SPF, and DMARC, including specific details about body hash failures, so you can diagnose and fix problems efficiently. Our platform makes DMARC accessible to everyone, from SMBs to large enterprises and MSPs.
Suped's DMARC monitoring platform to provide clear, actionable insights into your email authentication status. You can quickly identify issues related to DKIM, SPF, and DMARC, including specific details about body hash failures, so you can diagnose and fix problems efficiently. Our platform makes DMARC accessible to everyone, from SMBs to large enterprises and MSPs.