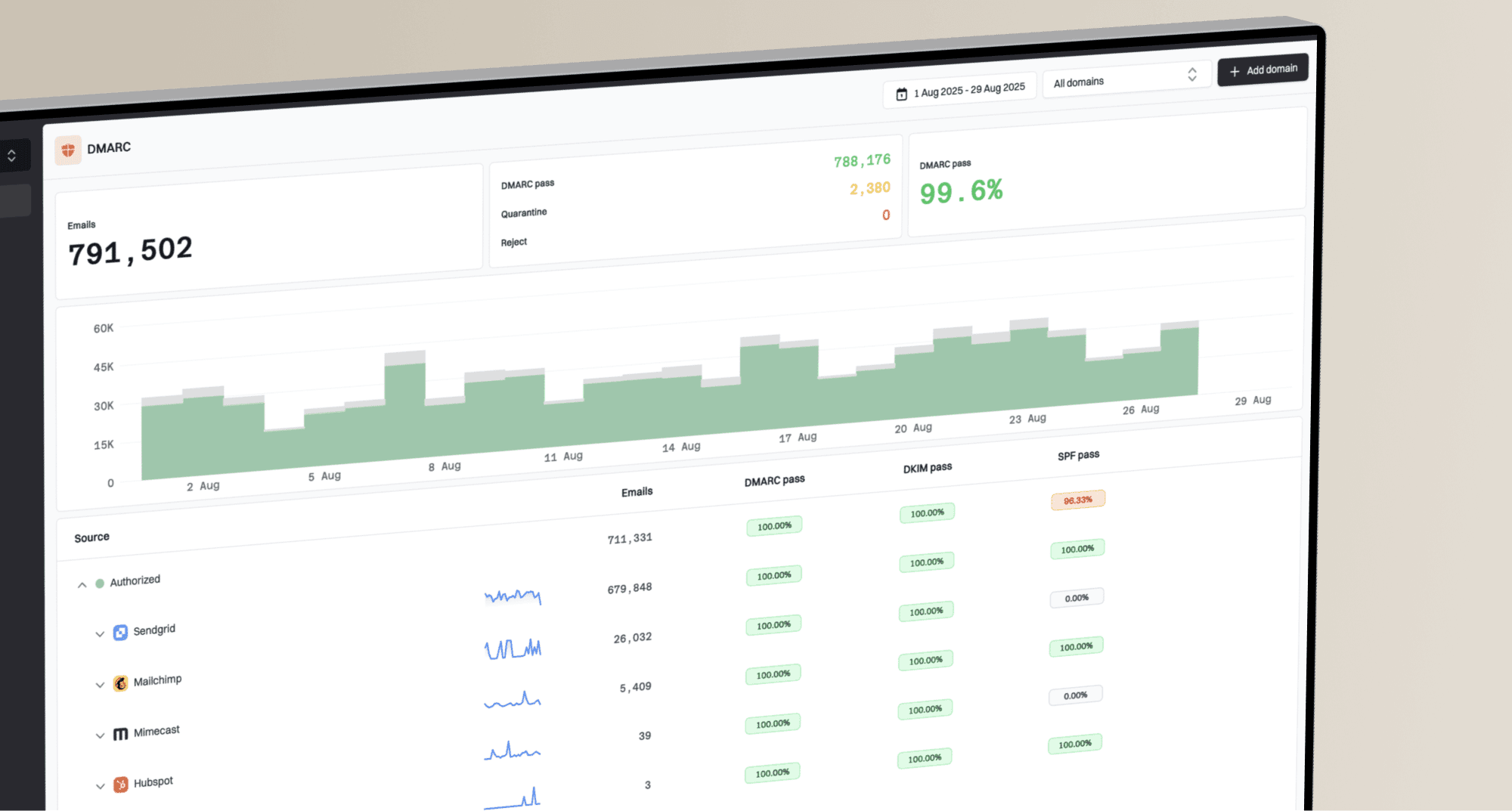
Does ARC require a DNS record for setup?

Michael Ko
Co-founder & CEO, Suped
Published 20 Jul 2025
Updated 28 Sep 2025
7 min read


arc._domainkey.example.com. IN TXT "v=ARC1; s=arc-selector; d=example.com; c=relaxed/simple; i=1; a=rsa-sha256; h=from:to:subject:date; bh=; b=..."
|
|
|
|---|---|---|
Selector | Often 'arc' or similar, identifies the specific ARC record. | Points to the correct public key in DNS. |
Domain | The intermediary's domain that is sealing the message. | Used by receivers to look up the ARC-Set record. |
Public Key | Contained within the TXT record, used for cryptographic verification. | Validates the ARC-Seal header's signature. |
 Start your DMARC monitoring journey today.
Start your DMARC monitoring journey today.