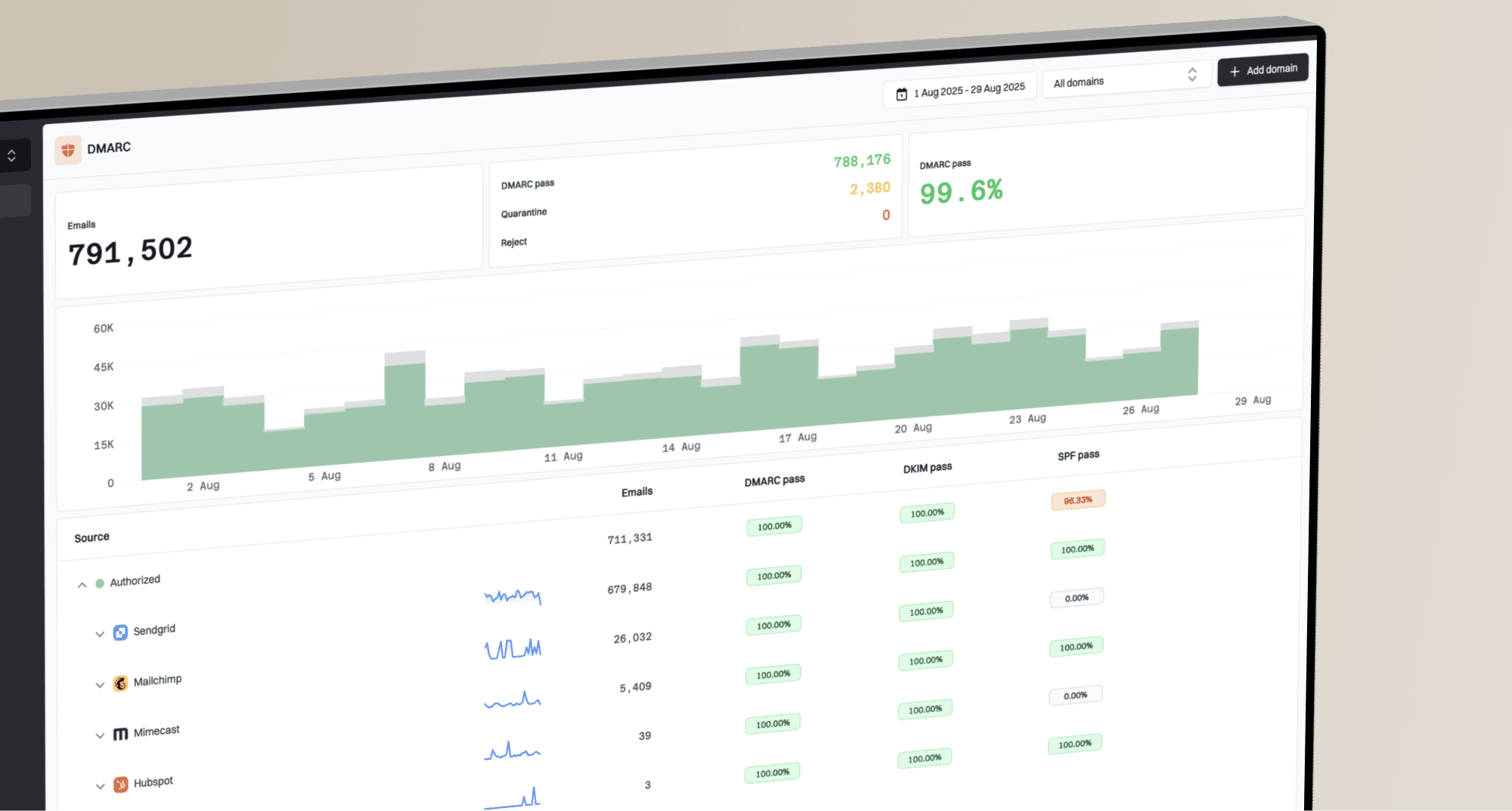
v=DMARC1; p=none; rua=mailto:dmarc-reports@example.com;v=DMARC1; p=none; rua=mailto:dmarc-reports@example.com; ruf=mailto:dmarc-forensic@example.com; fo=1;v=DMARC1; p=quarantine; pct=10; rua=mailto:dmarc-reports@example.com;v=DMARC1; p=quarantine; rua=mailto:dmarc-reports@example.com;v=DMARC1; p=reject; rua=mailto:dmarc-reports@example.com;v=DMARC1; p=reject; rua=mailto:dmarc-reports@example.com; ruf=mailto:dmarc-forensic@example.com; fo=1;v=DMARC1; p=reject; sp=quarantine; rua=mailto:dmarc-reports@example.com;v=DMARC1; p=reject; adkim=s; aspf=s; rua=mailto:dmarc-reports@example.com;v=DMARC1; p=reject; sp=reject; adkim=s; aspf=s; rua=mailto:dmarc-reports@bank.com; ruf=mailto:security@bank.com; fo=1;v=DMARC1; p=quarantine; sp=none; rua=mailto:dmarc@store.com; pct=100;v=DMARC1; p=quarantine; rua=mailto:admin@smallbiz.com;v=DMARC1; p=none; rua=mailto:dmarc-reports@example.com; ruf=mailto:dmarc-forensic@example.com; fo=1;v=DMARC1; p=none; rua=mailto:dmarc-reports@example.com; ruf=mailto:dmarc-forensic@example.com; fo=0:1:d:s; ri=3600;v=DMARC1; p=none; rua=mailto:dmarc-reports@example.com;v=DMARC1; p=quarantine; pct=10; rua=mailto:dmarc-reports@example.com;v=DMARC1; p=quarantine; pct=50; rua=mailto:dmarc-reports@example.com;v=DMARC1; p=quarantine; rua=mailto:dmarc-reports@example.com;v=DMARC1; p=reject; rua=mailto:dmarc-reports@example.com;