A brief history of email blacklists and blocklists



When you send an email, you expect it to land in the recipient's inbox. But behind the scenes, a complex system of checks and balances is working to protect users from the tidal wave of spam that floods the internet every day. At the heart of this system is a concept that has been around almost as long as spam itself: the email blacklist. These lists, now more commonly referred to as blocklists, are essentially databases of IP addresses and domains that have been identified as sources of unwanted email.
The terminology itself has evolved, with many in the industry moving from "blacklist" to the more neutral term "blocklist" to describe these mechanisms. Regardless of the name, their purpose remains the same: to act as a first line of defense for mailbox providers. Understanding their history is key to understanding how email deliverability works today. It's a story of innovation, adaptation, and a constant cat-and-mouse game between spammers and the people trying to stop them.
Over the years, I've seen these systems grow from simple, community-managed text files into sophisticated, data-driven platforms. Let’s take a look back at how email blacklists and blocklists came to be, how they’ve changed, and why they are still a critical component of the email ecosystem that every sender needs to understand.
In the mid-1990s, the internet was a very different place. Commercial email was in its infancy, and the concept of spam was just beginning to emerge. Initially, blocking unwanted email was a manual process handled by individual system administrators who would create their own rudimentary lists of troublesome IP addresses. It was inefficient and reactive, but it was a start. As the volume of spam grew, it became clear that a more centralized and automated solution was needed.
This led to the creation of the first DNS-based blocklist (DNSBL), the Real-time Blackhole List (RBL), in 1997. The concept was revolutionary for its time. Instead of every administrator maintaining their own list, they could now query a single, publicly available database in real-time. A mail server receiving an email could perform a quick DNS lookup to see if the sending IP address was on the RBL. If it was, the email could be rejected outright.
This new model was incredibly effective and quickly adopted. It marked a major turning point in the fight against spam. For the first time, the anti-spam community had a scalable, collaborative tool. Early blocklists were fairly simple by today's standards, primarily focusing on the IP addresses of open relays- misconfigured mail servers that spammers could exploit to send their mail anonymously.

As we entered the 2000s, spammers adapted. They moved away from using open relays and started building their own networks of compromised computers, known as botnets, to send spam. The simple IP-based blacklists of the 90s were no longer enough. The industry needed a more sophisticated approach, and new, more powerful blocklist operators emerged to meet the challenge.
Organizations like The Spamhaus Project and SpamCop became major players. They developed more advanced methods for identifying spam sources. Spamhaus, for example, built a global network of researchers and sensors to identify not just single spam-sending IPs, but entire networks controlled by professional spammers. SpamCop took a different approach, crowdsourcing spam reports from millions of users to identify active spam campaigns.
Another key innovation during this period was the development of domain-based blacklists. Spammers could switch IP addresses with relative ease, but their domain names were often a more consistent part of their campaigns, appearing in email content and links. Domain blocklists (DBLs) allowed mail servers to scan the body of an email for malicious domains, adding another powerful layer of protection and making it harder for spammers to evade detection.
As blocklists became more influential, they also became more controversial. The biggest issue was the problem of false positives. A legitimate business could find its IP address or domain on a blacklist by mistake, perhaps due to a temporary server misconfiguration, a compromised user account, or simply being on a shared IP with a bad actor. Being blocklisted could be catastrophic, cutting off communication with customers and partners.
In response, blocklist operators created formal delisting procedures. These processes required senders to investigate and fix the root cause of the problem before requesting removal. This shifted some of the responsibility back to the senders, encouraging better email practices across the board. It was no longer enough to just send email; you had to be a good internet citizen.
Around the same time, major mailbox providers like Gmail, Yahoo, and Microsoft began investing heavily in their own internal filtering technologies. They started looking beyond public blocklists, developing machine learning models that analyzed thousands of signals for each incoming email. These signals included sender reputation, user engagement (opens, clicks, and spam complaints), and authentication status. Public blacklists became one signal among many, rather than the sole decision-maker.
 Spamhaus
Spamhaus 0Spam
0Spam Cisco
Cisco NoSolicitado
NoSolicitado URIBL
URIBL abuse.ro
abuse.ro ALPHANET
ALPHANET Anonmails
Anonmails Ascams
Ascams BLOCKEDSERVERS
BLOCKEDSERVERS Calivent Networks
Calivent Networks EFnet
EFnet
 JustSpam
JustSpam Kempt.net
Kempt.net
 NordSpam
NordSpam RV-SOFT Technology
RV-SOFT Technology
 Scientific Spam
Scientific Spam Spamikaze
Spamikaze SpamRATS
SpamRATS SPFBL
SPFBL Suomispam
Suomispam System 5 Hosting
System 5 Hosting Team Cymru
Team Cymru Validity
Validity www.blocklist.de Fail2Ban-Reporting Service
www.blocklist.de Fail2Ban-Reporting Service ZapBL
ZapBL 2stepback.dk
2stepback.dk Fayntic Services
Fayntic Services ORB UK
ORB UK technoirc.org
technoirc.org TechTheft
TechTheft Spamhaus
Spamhaus 0Spam
0Spam Cisco
Cisco NoSolicitado
NoSolicitado URIBL
URIBL abuse.ro
abuse.ro ALPHANET
ALPHANET Anonmails
Anonmails Ascams
Ascams BLOCKEDSERVERS
BLOCKEDSERVERS Calivent Networks
Calivent Networks EFnet
EFnet
 JustSpam
JustSpam Kempt.net
Kempt.net
 NordSpam
NordSpam RV-SOFT Technology
RV-SOFT Technology
 Scientific Spam
Scientific Spam Spamikaze
Spamikaze SpamRATS
SpamRATS SPFBL
SPFBL Suomispam
Suomispam System 5 Hosting
System 5 Hosting Team Cymru
Team Cymru Validity
Validity www.blocklist.de Fail2Ban-Reporting Service
www.blocklist.de Fail2Ban-Reporting Service ZapBL
ZapBL 2stepback.dk
2stepback.dk Fayntic Services
Fayntic Services ORB UK
ORB UK technoirc.org
technoirc.org TechTheft
TechTheft Spamhaus
Spamhaus 0Spam
0Spam Cisco
Cisco NoSolicitado
NoSolicitado URIBL
URIBL abuse.ro
abuse.ro ALPHANET
ALPHANET Anonmails
Anonmails Ascams
Ascams BLOCKEDSERVERS
BLOCKEDSERVERS Calivent Networks
Calivent Networks EFnet
EFnet
 JustSpam
JustSpam Kempt.net
Kempt.net
 NordSpam
NordSpam RV-SOFT Technology
RV-SOFT Technology
 Scientific Spam
Scientific Spam Spamikaze
Spamikaze SpamRATS
SpamRATS SPFBL
SPFBL Suomispam
Suomispam System 5 Hosting
System 5 Hosting Team Cymru
Team Cymru Validity
Validity www.blocklist.de Fail2Ban-Reporting Service
www.blocklist.de Fail2Ban-Reporting Service ZapBL
ZapBL 2stepback.dk
2stepback.dk Fayntic Services
Fayntic Services ORB UK
ORB UK technoirc.org
technoirc.org TechTheft
TechTheft Spamhaus
Spamhaus 0Spam
0Spam Cisco
Cisco NoSolicitado
NoSolicitado URIBL
URIBL abuse.ro
abuse.ro ALPHANET
ALPHANET Anonmails
Anonmails Ascams
Ascams BLOCKEDSERVERS
BLOCKEDSERVERS Calivent Networks
Calivent Networks EFnet
EFnet
 JustSpam
JustSpam Kempt.net
Kempt.net
 NordSpam
NordSpam RV-SOFT Technology
RV-SOFT Technology
 Scientific Spam
Scientific Spam Spamikaze
Spamikaze SpamRATS
SpamRATS SPFBL
SPFBL Suomispam
Suomispam System 5 Hosting
System 5 Hosting Team Cymru
Team Cymru Validity
Validity www.blocklist.de Fail2Ban-Reporting Service
www.blocklist.de Fail2Ban-Reporting Service ZapBL
ZapBL 2stepback.dk
2stepback.dk Fayntic Services
Fayntic Services ORB UK
ORB UK technoirc.org
technoirc.org TechTheft
TechTheft Spamhaus
Spamhaus 0Spam
0Spam Cisco
Cisco NoSolicitado
NoSolicitado URIBL
URIBL abuse.ro
abuse.ro ALPHANET
ALPHANET Anonmails
Anonmails Ascams
Ascams BLOCKEDSERVERS
BLOCKEDSERVERS Calivent Networks
Calivent Networks EFnet
EFnet
 JustSpam
JustSpam Kempt.net
Kempt.net
 NordSpam
NordSpam RV-SOFT Technology
RV-SOFT Technology
 Scientific Spam
Scientific Spam Spamikaze
Spamikaze SpamRATS
SpamRATS SPFBL
SPFBL Suomispam
Suomispam System 5 Hosting
System 5 Hosting Team Cymru
Team Cymru Validity
Validity www.blocklist.de Fail2Ban-Reporting Service
www.blocklist.de Fail2Ban-Reporting Service ZapBL
ZapBL 2stepback.dk
2stepback.dk Fayntic Services
Fayntic Services ORB UK
ORB UK technoirc.org
technoirc.org TechTheft
TechTheftToday, the world of email deliverability is a complex tapestry of public blocklists, private reputation systems, and sophisticated inbox provider filters. While the influence of public blacklists may have diminished from their peak, they are far from irrelevant. Getting listed on a major, reputable blocklist like Spamhaus is still a very strong negative signal that can have an immediate and severe impact on your ability to reach the inbox.
Mailbox providers see a listing as a clear indicator of a problem. Even if they don't block your mail outright based on the listing alone, it will heavily weigh down your overall sender reputation, making it much more likely your emails will be filtered to the spam folder. Common reasons for getting blacklisted in the modern era include:
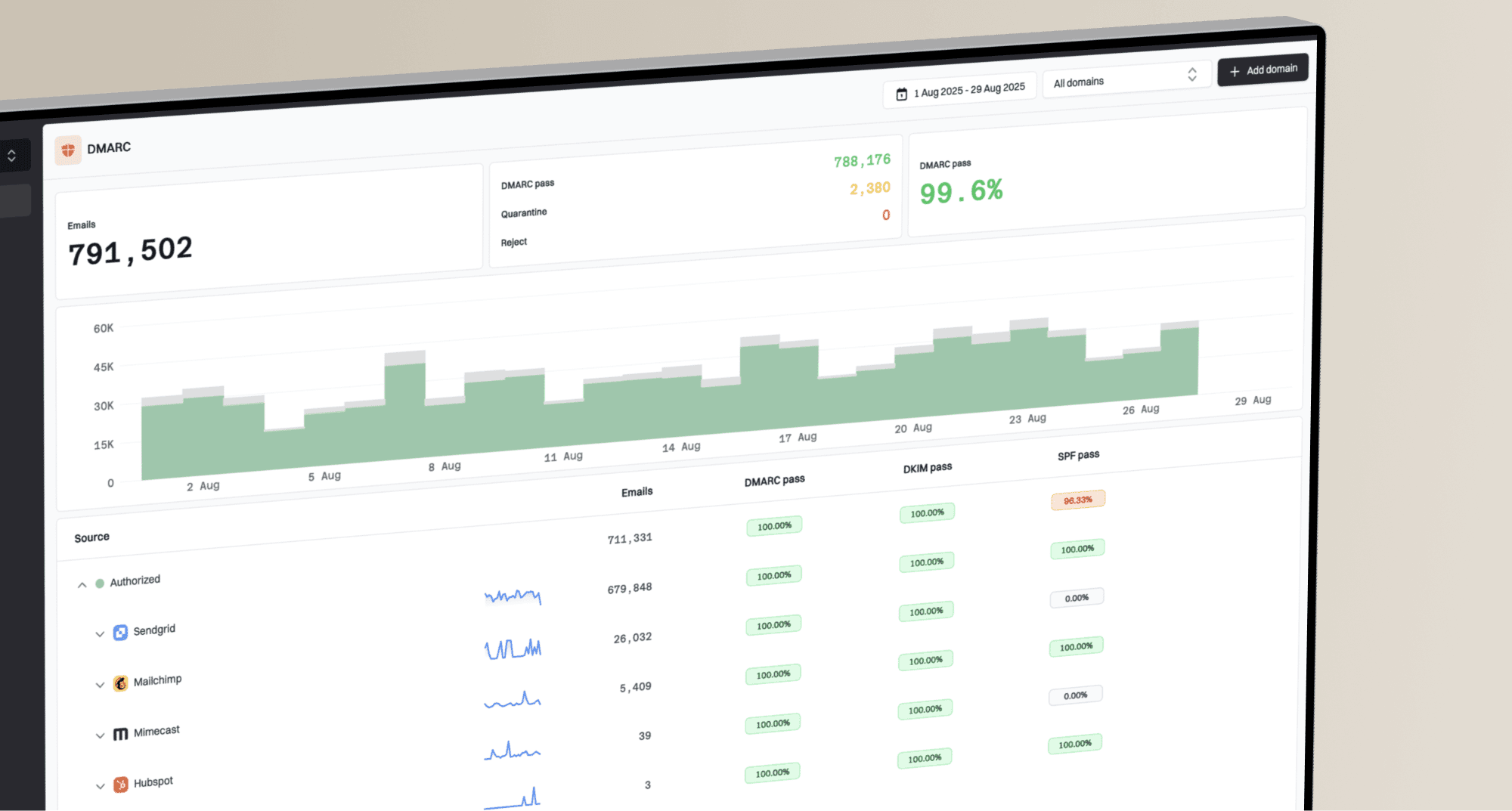
This is why proactive monitoring is so essential for any serious sender. You can't just assume your domains and IPs are clean. You need to actively check them against the most important blocklists. This is a core part of what we do at Suped, providing a clear and constant view of your sending reputation so you can address issues before they cause major delivery problems.
The history of email blacklists is the history of the internet's immune system. From the simple RBL of the 1990s to the multifaceted ecosystem of today, these tools have been instrumental in keeping our inboxes usable. While their role has changed, their fundamental importance has not. For anyone sending email, understanding this history is the first step toward building a strong sender reputation and ensuring your messages get where they need to go.