I have been spending a lot of time recently reviewing the upcoming updates to the DSI SMB1001:2026 standard, specifically the changes to the Email Authentication and Anti-Spoofing controls. If you are an SMB or an MSP managing compliance, you need to pay close attention to this. The bar has been raised significantly.
In the past, basic email security was often a "nice to have" or limited to simple SPF records. The 2026 update changes that dynamic entirely. The new standard explicitly differentiates between "Silver" and "Gold" tiers, and the gap between them is where most businesses are going to struggle.
Here is what the changes look like and how you should approach them to avoid disrupting your business operations.
The Silver Tier: The New Minimum
Looking at the new control 2.12.0.0 (Silver), the requirement is straightforward but non-negotiable.
i) Configure Sender Policy Framework (SPF) on all domains used to send organizational email to prevent spoofing and protect recipients.

For the Silver tier, you are required to have a valid SPF record. This is the "ID card" for your email server. It tells the world which IP addresses are allowed to send emails on your behalf.
Most businesses I audit at
Suped already have this in place, but it is often misconfigured. The standard explicitly notes that "implementation and maintenance of SPF records can be complex." This is true. If you use Google Workspace, Mailchimp, and a CRM like Salesforce, you need to ensure all of them are listed in your SPF record. If you miss one, your emails might start landing in spam folders even at the Silver level.

The Gold Tier: The Big Leap to Enforcement
This is where things get serious. The update for 2.12.1.0 (Gold) introduces a comprehensive trio of security protocols: SPF, DKIM, and DMARC.

If you want to achieve Gold certification, you can no longer ignore DMARC. The requirements are specific:
- SPF: Continue maintaining valid records.
- DKIM: Enable cryptographic signing on all outbound email. The standard mandates 1024-bit keys as a minimum, but practically, you should be aiming for 2048-bit keys where supported.
- DMARC: This is the critical change. You must publish a DMARC policy in your DNS.
The most aggressive part of this update is requirement iii(c):
"Set DMARC policy to p=reject or p=quarantine (not p=none)"
This is a massive shift. Setting a policy to `p=none` is the standard "monitoring" mode that most companies sit in for years. It allows you to see who is sending email as you, without blocking anything. The DSI SMB1001:2026 Gold standard effectively says "monitoring is not enough—you need enforcement."
The Danger of Rushing to "Reject"
I cannot stress this enough: Do not log into your DNS provider and flip your policy to `p=reject` today just to tick a compliance box.
If you do this without proper visibility, you will almost certainly block legitimate emails. I have seen companies lose invoices, contract renewals, and marketing campaigns because they enforced DMARC before they knew exactly who was sending mail on their behalf.
The standard acknowledges this risk in the notes, stating that enforcement is a "complex process that requires careful monitoring."
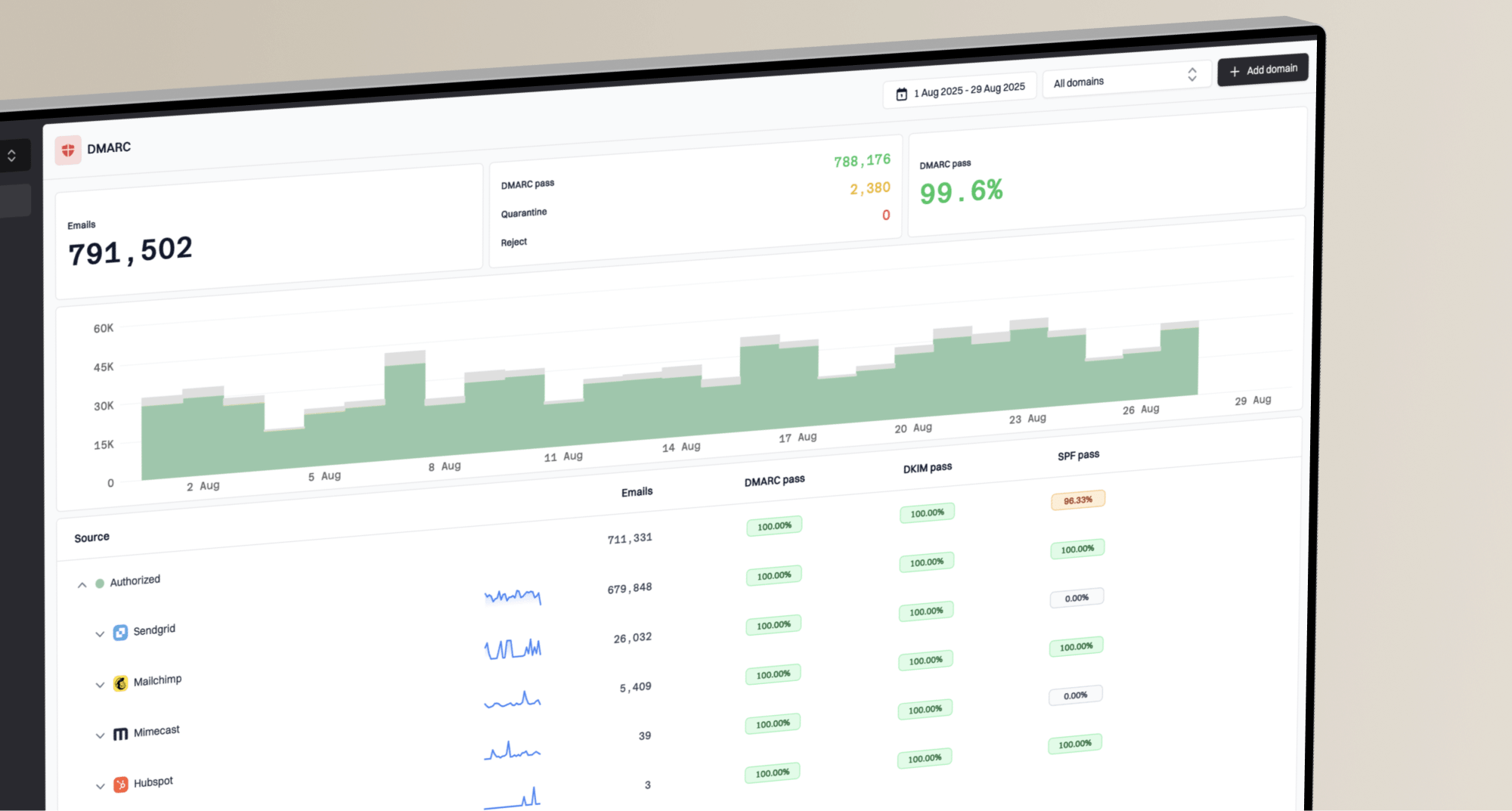
This is why platforms like ours exist. You need a period of "monitoring" (p=none) where you gather data on every service sending email as your domain. You might find that your HR platform or your invoicing software is failing authentication. You have to fix those first. Only once you are 100% sure that all your legitimate services are authenticated (aligned with SPF and DKIM) should you move to `p=quarantine` or `p=reject`.

How to Meet the Requirement Safely
To comply with DSI SMB1001:2026 without breaking your email flow, follow this workflow:
- Audit Your Senders: Use a tool (like Suped) to capture reports on everyone sending email from your domain. You will be surprised by how many "shadow IT" services are sending mail you didn't know about.
- Configure DKIM: The Gold standard requires DKIM signing. Log into your email providers (Google, Office 365, HubSpot, etc.) and turn on DKIM. This attaches a digital signature to your emails that proves they haven't been tampered with.
- Align Your Protocols: Ensure that the "From" address in your emails matches the domain in your SPF and DKIM records. This "alignment" is crucial for passing DMARC.
- Monitor, Then Enforce: Start at `
p=none`. Watch the reports for a few weeks. Once the "fail" rate for legitimate traffic drops to zero, move to `p=quarantine`, and finally `p=reject`.
Why This Matters Beyond Compliance
While hitting the Gold standard is a great goal, the real benefit here is security. By enforcing DMARC, you are effectively stopping bad actors from spoofing your domain. It makes it incredibly difficult for hackers to send phishing emails that look like they came from your CEO or finance team.
For more details on the specific controls, you can review the full
SMB1001 Standard.
The 2026 updates are pushing the industry in the right direction. It is no longer acceptable to leave your domain wide open to impersonation. If you are preparing for your audit or just want to secure your domain, start your monitoring journey now or get in touch with us at Suped.